More Cryptography
By Austin Chamberlain, on 10 March 2017
My colleague Gen gave a very good primer on the basics of cryptography last week. In this post I’ll expand some more on the theory of cryptography, and in my next post I’ll talk about some of the main applications.
It is only in the last forty or so years that cryptography has been a formal science with mathematical backing. Prior to the 1970s, cryptosystems were usually designed in isolation and had little in the way of mathematical proof for their strength. It is the development of cheap, fast computing that has allowed cryptography to become a routine activity, and large amounts of theoretical work by government and academia in the 1970s on has created a systematic way of developing cryptosystems and proving their strength (or lack thereof!).
Terminology
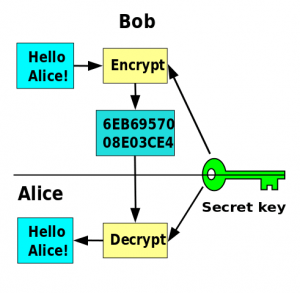
Symmetric encryption, or “secret key encryption”
Cryptography means literally “secret writing”. The parties communicating in cryptography are usually called Alice, “A” and Bob, “B”. A third party trying to eavesdrop on their communications is usually called Eve, “E”. We talk about ciphers, rather than codes – codes and encoding are a means of representing some message in another format, and in do not specifically imply secrecy.
Gen mentioned asymmetric cryptography, with a public and a private key. This is often referred to as “public-key cryptography”, because of the fact that one of the keys is public. Other encryption is called symmetric, because the same key is used for both encryption and decryption. This key has to be kept secret, thus symmetric cryptography is also called “secret-key cryptography”. A key feature of asymmetric encryption is that it is possible to establish a new, secret channel over a monitored communication channel – in other words, you can set up a secret session even if someone is watching every bit of traffic on your network connection. This is what you are doing every time you visit a secure website, or your Outlook mail client talks to the mail server.
I’ll explain one more cryptographic concept – the cryptographic hash. This is not a cipher as such. Instead, it’s a one-way, unique transformation of data of any length to a data string of a specific length, called the hash. One-way means you cannot find the original data from the hash, and unique means that different input data always produces a different hash.This might sound rather arbitrary and useless, but it is vital to the functioning of encryption systems.
Strength and Speed
Asymmetric encryption sounds like a better deal – you can set up a secure connection over a clear channel. Symmetric encryption is used far more often, however, because it is much faster and more space-efficient than asymmetric. The mathematical operations to perform asymmetric encryption (exponentiation or elliptic-curve calculations on big numbers) are much more demanding on a computer CPU than those for symmetric encryption. The usual process for a secure connection is for the client and server (browser and web server, Outlook and mail server) to perform a handshake with asymmetric encryption, use this secure channel to exchange a symmetric secret key, and then use symmetric encryption for the rest of the conversation.
Cryptosystems Become Obsolete
Computers are getting more powerful over time, and this has a specific meaning for cryptography. Systems that are strong when designed will usually be increasingly vulnerable to simple brute force attacks (trying every possible key against the encrypted message). Researchers will also work on the theory behind given cryptosystems, often finding weaknesses in the design or implementation, and leading to more efficient attacks.
A good example of this is the Digital Encryption Standard (DES), which is a US government standard first developed in the 1970s. This is a symmetric cipher with a 56-bit key size, and it has some very interesting features for the 1970s. IBM designed DES originally, and submitted it to the US government for approval. The National Security Agency (NSA) recommended some changes, and DES was accepted as a US government standard. Years later it was discovered that unclear changes recommended by the NSA at the time made DES more resistant to differential cryptanalysis (which was unknown at the time), and IBM admitted that this attack was known to IBM and the NSA at the time. Research has discovered other weaknesses in DES, however, and the short key length and cryptographic weaknesses means DES is no longer regarded as secure. It was first broken in 1997, and was replaced by AES (Advanced Encryption Standard) in 2002.
Some cryptosystems are designed with a variable key length, so keys can be made longer (and systems stronger) as required. Managing cryptosystems against performance and attacks is an ongoing process.
Next up – applications of cryptography!
Cryptography basics
By Gen Cralev, on 3 March 2017
Cryptography is a highly important concept within Information Security. You may not be aware of it, but we depend on cryptography on a daily basis to secure our data. Whenever you do online shopping, log in to Facebook or check your bank account balance, your information is automatically encrypted. We use encryption to ensure that if someone is able to obtain our data, they aren’t able to read it.
How does it work?
Encryption is the act of transforming information from a readable form (plaintext) into an encrypted form (ciphertext). For example, the text you are currently reading is in plaintext and is therefore unencrypted. To encrypt the text, we need to apply an algorithm or a mathematical formula that will change its content. The most well-known and simplest form of encryption is called the ‘Caesar cipher’. It is said to have been used by Julius Caesar to send secret military orders to his generals. The Caesar cipher works by shifting each letter of the plaintext by a certain number of letters. The number of letters we shift by acts as a key.

For example, if we shift each letter of the word “secret” by 3 we get a ciphertext output of “vhfuhw”. In order for the recipient to then transform the ciphertext back into plaintext, they simply apply the reverse action (shift 3 to the left). Check out this online tool that demonstrates the Caesar cipher in action: http://www.xarg.org/tools/caesar-cipher/. The Caesar cipher was sufficient to encrypt messages 20 centuries ago but it is no longer considered to be secure. Modern day encryption algorithms employ a highly complex formula to ensure that even the most powerful computer systems aren’t able to decrypt the data without the correct key.
The Caesar cipher falls under the category of symmetric cryptography. This means that the same key is used to decrypt the data as the one used to encrypt it. This poses the problem of key exchange. How do we ensure that only our intended recipient has the correct key? If we do not take sufficient precautions when providing our key to the recipient, it can easily be apprehended by a malicious third party rendering the whole process useless.
Asymmetric cryptography
Asymmetric cryptography solves the problem of key exchange by employing two mathematically related keys – a public key and a private key. The public key is shared with everyone and is used to encrypt the data we are sending. The private key, on the other hand, is used to decrypt the data and is only known to its owner. If I want to send an encrypted email to you, I would use your public key to encrypt the message. This ensures that only you are able to decrypt the message as your private key should only be known to you.
Asymmetric cryptography also allows us to sign messages in order to prove that we are the ones that sent them and they haven’t been altered in transit. This is done by encrypting the message using our private key. If others then use our public key to decrypt the message, this proves that the message came from us and is legitimate.
These are just some of the basic concepts within cryptography but they provide all sorts of possibilities to improve security in the digital world.
Password Complexity Matters
By Gen Cralev, on 1 March 2017
There is an endless supply of literature on the Internet about usernames and passwords. Yet this is an immensely important topic that will always be relevant.
Tom has already written a blog post about passwords from a risk perspective so I will approach the topic from another angle and explain why the complexity of your password can make a huge difference to the overall security of your information.
However, first it is necessary to take a look at the basic mechanisms behind usernames and passwords. From a security perspective, a username is simply a form of identification. When a system is asking you for a username, it is essentially asking you to identify yourself as a user of its resources. In its basic form, this is the equivalent of someone asking you for your name. You can reply however you like. Whether they believe you or not is a different matter. This is where a password comes in. When you provide your password, you are basically authenticating yourself as the person that the provided username belongs to. Only you should know the password corresponding to your username. This is the equivalent of providing a driver’s license or a passport to confirm that you are indeed who you say you are.
Problems with passwords
Now let’s consider a common problem in the information security world – a compromised account. What I’m referring to here is the case where someone other than the intended individual has access to a specific account. This can come about in a number of ways such as:
- Willingly sharing credentials (e.g. with your colleague)
- Shoulder surfing (the attacker looks over your shoulder while you are typing your password)
- Writing a password down and storing it insecurely (e.g. on a sticky note at your desk)
- Data leak (usernames and passwords are made publicly available without authorisation)
- Brute force/dictionary attacks (the attacker guesses the password. This is done either by trying out every possible combination or going through a dictionary of commonly used passwords)
In relation to most of the points above, but specifically the brute force/dictionary attack, a more complex password can significantly improve security. This comes down to the way that this specific attack is performed. A computer is highly efficient and can test a large number of passwords in a short period of time and the more computer power dedicated to the task, the quicker the password will be correctly guessed.
As you add extra complexity elements to your password (extra characters and different types of characters) you make it increasingly difficult for a computer to be able to successfully guess your password.
Here’s a fun tool to demonstrate this concept: https://howsecureismypassword.net/. Although we don’t recommend that you enter your actual password!
Greetings!
By Gen Cralev, on 28 February 2017
Hello. My name is Gen Cralev and I am an Information Security Support Analyst at the Information Security Group (ISG). That’s quite a long job title, but what does it mean? Primarily, I am the first point of contact for ISG. So if you call our office on +44 (0)20 7679 7338 or email isg@ucl.ac.uk it will most likely be me that you deal with initially. At that point, I will either assist you with your query, or pass it on to one of my colleagues if it relates to their area of expertise.
Goals
The fundamental goal of ISG is to protect the information assets of UCL and we achieve this in a number of ways. Some of the things that we do include:
- Conducting structured risk assessments
- Performing vulnerability scans and penetration tests on our systems
- Actively monitor systems for incoming, outgoing and internal attacks
- Responding to threats to our information assets
- Ensuring that relevant policies are up to date
- Raising awareness of potential risks and promoting best practice
See a more detailed list on our Service Catalogue page.
Later on this week I will write more in depth about some of the common queries that ISG faces and basic concepts of information security.
Policy Writing .. As easy as it sounds!
By utnvrrv, on 27 February 2017

Policy-Writing. One step at a time
This series of posts explains an effective policy writing process. It will take a reader through some of the steps involved in policy writing.
Policies as cornerstones
A policy reflects the organisation’s strategy for carrying out its functions. As an example, a Finance policy lays down the ground rules for effective adminstration of its finances that satisfies HMRC. Similarly, an Information Security policy should reflect the organisation’s objectives for security. This policy should satisfy its stakeholders that the data and information it holds is subject to the necessary controls. It also sets the framework for the management strategy for securing information.
Are we in agreement?
In order for any policy to work well, it must be agreed on by the executive management. With proper management support, the policy provides authority for executing the rest of the program, in this case the Information Security Program. It is important to understand the management thinking when defining a policy for the organisation. Besides, management support, the policy writer (security professional) should get the views of key stakeholders in the organisation. It is also important to understand the culture and the ethic of the organisation when defining a policy.
Positive Statement
Post the interviewing process, the policy writer must capture the essence of the discussions in a postive statement. This statement will illustrate how the organisation would like its information protected. The statement should be a faithful representation of views; that is, without overstatement, change of meaning or adding to the content.
Next steps
In the next blog we will look at molding management’s perspective on the subject and emerging with a strategy. Till then..
P|S|P|G – Simplified
By utnvrrv, on 24 February 2017
 We’ve all come across these terms in common parlance, but why not a refresher?
We’ve all come across these terms in common parlance, but why not a refresher?
Policy
This is a set of high level statements across the business. A policy identifies the issue and the scope. It consists of the What? and the Why? Policies deal with rules related to key issues. A policy contains a statement of intent. A policy could also be said to be a set of rules to abide by. An information security policy of an organisation is the intent to maintain the Confidentiality, Integrity and Availability of its data.
Standard
It may assign a quantifiable measure of achievement. It could also mean something used as a measure, norm, or model in comparative evaluations. The ISO/IEC 27001 standard is the world’s leading standard for information security management. It provides requirements for establishing, implementing, maintaining and continually improving an information security management system. It is intended to be applicable to businesses of all sizes and types.
Process
A Process defines a series of actions taken to achieve a particular end. A process is a set of activities that interact to achieve a result.
Guideline
A guideline provides additional recommended guidance.This ia a piece of advice on how to act in a given situation. A guideline is a recomendation of good practice and is non-mandatory.
I hope that I have simplified the difference between the terms and made it a bit more easier to understand. In the next blog post, I will look at the elements of a good policy process.
Policy, Policy, Policy.
By utnvrrv, on 21 February 2017

Hello, My name is Ravi and I work with the Information Security Group. My role is to refresh all the existing Information Security Policies and make them more current.
Definition
According to the Cambridge Dictionary, a policy is “a set of ideas or a plan of what to do in particular situations that has been agreed to officially by a group of people, a business organization, a government or a political party” I’m going to focus on the Information Security Policies and their role in being the guiding posts for UCL. Read on…
Why policies?
The development of security policies has become a critical component in all organisations. UCL recognizes the importance of information security in its day-to-day business. “Information security policies help UCL maintain its ability to prevent security incidents”. In addition to this, these policies help us to respond to security incidents when they do occur. UCL intends to have sound and robust policies. This assures all our stakeholders that their data and information is well protected.
Policies cannot be static and need to change with time. Some common drivers for policy change include:
- technology upgrade,
- new business rules coming into play, and,
- changes in legislation.
It is always a good idea to define a review timeline for a policy, this can be a year at the minimum.
Further reading
If you would like to read the information security policies, please see here: https://www.ucl.ac.uk/informationsecurity/policy/
Auto-phishing? Autocomplete security risks
By Tom, on 17 February 2017
Today I’m going to look at a specific security flaw and how to think about this from an information risk perspective.
You may have seen articles about malicious websites exploiting browser autocomplete. Basically, criminals create a malicious page that looks legitimate, and include a couple of fields for text entry, say, name and email address. They also create other fields that capture more, possibly sensitive information (e.g. address, phone number, password, etc.), and then hide these fields so that they’re not visible to website visitors. You visit the page, autocomplete fills all the boxes, including the ones that you can’t see, and you unwittingly submit more information that you intended. Without realising it you can accidentally give away your password.
Obviously this is no good. We want to browse safely and conveniently, and autocomplete is just an automatic component of most browsers now.
Let’s express this in terms of a risk:
“Due to my accounts being compromised by malicious websites harvesting my password via hidden autocomplete fields, my confidential information is at risk of unauthorised access.”
To manage the risk, we need to select a management action. These fall into four categories:
- Treat: Treating a risk means taking an action to control the risk, reducing the chances that it will occur. This means making the attack harder to achieve, for example by disabling autocomplete.
- Transfer: Transferring means arranging for a third party to be impacted if the risk occurs. Taking out insurance is an example of transferring risk. Transferring is probably not an option in this case.
- Tolerate: Tolerating risk is self explanatory; it is accepting it as “the price of doing business”. In this case it would mean not adjusting our behaviour at all.
- Terminate: Terminating a risk means avoiding the activity that creates the risk in the first place. In this case this could mean avoiding the use of any of the accounts we are discussing.
The most suitable action here is to treat the risk. A simple fix would be to disable the autocomplete function in your browser. In conjunction with something like LastPass (see a previous post), you can securely store your information in such a way that you don’t need to use autocomplete to retain useful login information.
Note: It is possible to use LastPass to autocomplete forms too. This may also be prone to the vulnerability discussed here. You can however disable autocomplete here too and simply reference your stored information. This again helps to treat the risk.
Password risks and how to treat them
By Tom, on 15 February 2017
We are all drowning in password advice and I’m loath to add my name to the seemingly endless list of “security people berating bad password practice”, but if you try to apply an information risk management viewpoint to a lot of areas where we store private information, both in our work and private lives, it is still all too often the case that a username and a password are the only elements controlling access to vast tracts of our lives.
Or, in other words, if I’m going to discuss practical information risk advice, then I need to discuss passwords. I’ll keep it brief I promise.
P@55w0rd is ok right..?
There is plenty of good advice available on how to write a strong password. Instead, I’m going to talk about how to remember all those long, complex passwords. If you can make it easy to manage all these different accounts then you can remove the motivation to use weak, or duplicate passwords.
Password managers are tools that allow you to do just this. A password manager allows you to create a single strong password, and use that to encrypt a vault containing the logins to all your remaining accounts. What this means is that you can create a highly complex password for each site, but without the added overhead of having to remember these complicated strings.
Let’s apply that to an example risk
“There is a risk that my information may be accessed by unauthorised actors as a result of my password being guessed, or duplicated from another site that has been hacked”
You can calculate risk as a function of a threat (unauthorised access) due to a vulnerability (password being compromised) resulting in an impact (the consequences of the unauthorised access).
We can reduce the risk by controlling any one of these factors. Practically speaking we can’t reduce the chances that someone may try and hack an account. Similarly, we can’t do much to reduce the value that other people ascribe to our information. What we can do however, is reduce the chance that they will be successful. By using a password manager (and creating strong passwords) we have reduced the likelihood that someone will compromise our password. Reducing the liklihood has reduced the risk.
Of the many tools available, ISG have reviewed the two below and can recommend them as offering reasonable assurance:
- LastPass https://lastpass.com/
- Password Safe https://pwsafe.org/
Introduction to information risk
By Tom, on 15 February 2017
My name is Tom Seeler and I work for the Information Security Group doing information risk management. What this means in practice is that I work with people all across the university to help them identify risks to their information as a result of the work that they are doing. This can range from data they are gathering as part of a study or how to share files within their team, through to helping to understand the implications of providing a new service to office staff. Regardless of the specifics of the risk assessment, my first questions are usually “what is the information you are working with” and “where is it going”?
They’re deceptively simple questions but it can lead to some really interesting discussions. You can’t have actual control over your information if you can’t answer them, and you can’t work out how to protect yourself if you don’t know what you’re protecting. Just as important is when you arrive at an “I don’t know”; the first step to removing the confusion is to identify it.
It’s an interesting exercise to apply to the things you work with every day, whether it’s a private social media account or a document workflow at school or your job. Where exactly is valuable information being stored and, now that you’ve visualised it, are you comfortable with how it is protected. These are the basics of risk assessment and I will be going into more detail in my future posts, as well as offering what I hope will be useful and practical advice on reducing information risks.
 Close
Close


