Sophisticate Attacks
By Daniela Cooper, on 28 January 2026
Meet Sophie. Sophie is a security consultant. She gets paid to think like a criminal and break into buildings.
Organisations hire Sophie to test their security.
Sophie uses fake emails, phone calls and text messages to pretend to be someone she’s not. Much of the time, she approaches people in person and manipulates them to help her.
Sophie’s attacks are “sophisticated” because she targets individuals. Sophisticated attacks work by getting people to do things they wouldn’t usually do, like provide access to restricted information or areas, pay “invoices”, or break policy.
Sophisticated attacks are often called “social engineering” attacks.
Recently, a client hired Sophie to test two of their facilities: a manufacturing plant and a nearby office.
This is how she did it…
Stage 1: Research
Your social media accounts are Sophie’s best friend. The more information you share, the more options you give her.
Sophie has several fake profiles. You might even be connected to one. (A good reason to always verify who people are before accepting requests.)
Sophie started by using one of her accounts to look for people who worked at the facilities. She found a Facebook account of a young woman, “Mary”.
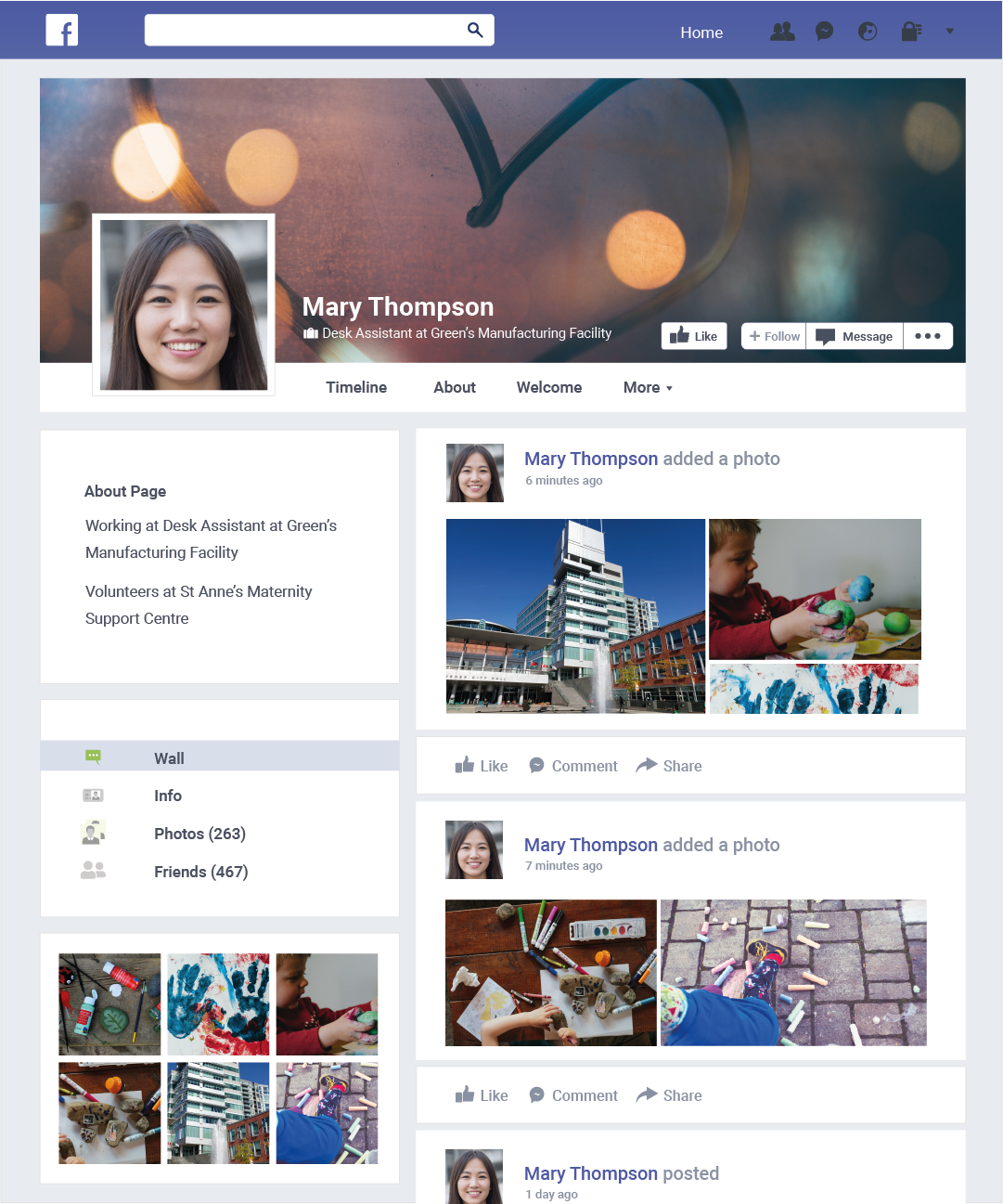
Mary worked as a front desk assistant at the manufacturing facility.
Mary’s Facebook profile showed pictures of her volunteering at a maternity support centre. Sophie could tell Mary cared for children and new mothers. Of course, she would use this to her advantage.
Stage 2: Setting the scene
Sophie knew she would more likely be welcomed into the facility if staff were expecting her. So, she went about setting the scene for her arrival.
Armed with the knowledge about Mary, Sophie picked up the phone.
Before dialling, Sophie disguised her phone number so it looked like she was calling from head office. This process is known as “spoofing”.
Spoofing: When emails, phone calls and text messages are made to look like they’re from someone else.
By spoofing her client’s head office phone number, Sophie added credibility to her attack. Spoofing works because people don’t always verify who they’re talking to.
Pro Tip
What to look out for: Phone calls
All phone numbers can be faked. This includes internal extensions.
Criminals pose as legitimate people, like bank staff or IT teams. Their aim is to convince targets to do things they wouldn’t usually do.
Control your emotions, especially if the caller tries to get you to panic, worry, or act under pressure. Don’t do things you wouldn’t normally do. Stick to policy.
When necessary, verify. Call back using a known contact number (either that you know or that’s published online).
What to look out for: Text messages
Criminals also use fake text messages to encourage people to:
- Click links that lead to fake websites. Fake websites are set up to steal personal details or install malware.
- Call numbers that connect to criminals, or premium-rate lines.
Fake text messages can even drop into ongoing conversation threads with genuine contacts!
It’s rare for us to advise never to do something. Text messages are the exception. There’s no way to determine the real sender of a text message, so:
- Never click links in texts.
- Never follow directions sent via text.
- Don’t do things you wouldn’t normally do. Stick to policy.
- Verify if you need to, search online for legitimate details.
All suspected fake phone calls and text messages should be reported.
“Hi Mary! My name is Barbara.”
Sophie got right to it. She explained she was “Barbara”, a project coordinator arranging the refurbishment of company offices.
Sophie told Mary she was sending an interior designer out the next day. The interior designer, Sophie said, was putting together a facility-update proposal.
Mary was cautious, “Well, that’s great! But why the short notice?”
It was time for Sophie to play her trump card.

All phone numbers can be faked. This includes internal extensions.
Sophie explained she should have called sooner. But she was overloaded with work and was due to give birth in six weeks, “If my boss finds out I messed this up he’s going to flip.”
Mary cut her off. “Oh, it’s ok. We’ll work this out! Tell me about the baby! Is it your first? Boy or girl?!”
Mary was hooked. She was a good person, who just wanted to help.
The two talked babies and birth plans for a while. Mary then took down the name of the designer who would visit the next day, “Claire”.
If only Mary had verified who she was talking to. If only she had hung up and called back.
But she didn’t…
Stage 3: Attack
Sophie showed up the next day as “Claire” the interior designer. Claire had her own business cards and website! (Sophie had made them the night before.)
Mary and her boss were waiting to welcome Sophie. She shook hands and handed them each a business card. Mary gave Sophie a visitor badge and invited her in.

Sophie gained rapport with the staff by asking them what they wanted from an office space. “You want a standing desk? New chairs over here?! Ergonomic keyboards for all!!”
Everyone was very excited.
Sophie took forever looking around. Eventually Mary and her colleagues had to get back to work. They left Sophie, giving her complete, unaccompanied access to both facilities.
The company had a policy of escorting visitors. But because Sophie had been seen with trusted insiders, no one questioned her. She was free to do as she pleased.
Pro Tip
What to look out for: In-person approaches
In-person approaches rely on our desire to help. This shouldn’t be discouraged.
We should trust the people around us, but we also need to be comfortable checking if something doesn’t look or feel right.
Procedure is well thought out. It’s there to support and protect. A genuine person without ID won’t be annoyed or angry if you politely ask who they are and why they’re in the building. Trust, but verify.
What to look out for: Shoulder surfing
“Shoulder surfers” are opportunists who check screens or listen to private conversations.
When working in a shared space:
- keep your desk clear to prevent loss of physical assets,
- and consider who’s around before discussing sensitive topics.
Just like you would be with your PIN at an ATM, or whilst on the phone to your bank.
A privacy screen is a thin piece of plastic that’s placed over your monitor. It stops people seeing what’s on your screen.
What to look out for: Fake USB devices
Fake USB devices are USB devices that damage or steal data from computers or networks.
Any USB device can be harmful. This includes charging cables.
Labels like “bonus payments” can make USBs enticing. Letting curiosity take over can be risky.
Report any stray USB devices you find. Plugging them in isn’t worth it.
Sophie took her time. She gained network access and stole several thousand dollars worth of computer equipment.
Once she’d finished, Sophie found the office of the person who’d hired her…
“Who?…. Wait, what? How? How did you get in here?!”
Sophie sat down and smiled, “Let me start from the beginning…”
Summary
Everyone should be able to do their job without worrying about sophisticated attacks.
Trust those around you. But recognise when you’re being steered by emotions. Be comfortable checking when things aren’t right.
Don’t panic if you accidentally click, say, or do something unwise in an odd moment. It’s okay as long as it’s reported. Reporting buys time. It prevents further damage.
Stopping sophisticated attacks: “Trust, but verify”
1. All emails, phone calls and text messages can be made to seem as if they’re from someone else.
2. If you receive a request you weren’t expecting, or one that has an undue sense of urgency, slow down. Verify and follow policy.
3. If you think you’ve identified a sophisticated attack, report it. Reporting prevents cyber crime.
“Sophie” is a real person. Her story was adapted from the original published on vice.com on 20th October 2017.
With thanks to CybSafe for providing this content.
Fake CAPTCHA Phishing Attacks
By Peter Andrews-Briscoe, on 2 December 2025
Written by Bassit Mayet
Summary
During 2025, there were reports from different reputable sources of an increase in the use of fake CAPTCHA verification pages to trick users into downloading and running malicious code.
Fake CAPTCHA malware refers to a social engineering scam where cybercriminals create deceptive CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) challenges on websites to trick users into self-infecting their devices with malicious software. These fake CAPTCHAs mimic legitimate ones—such as the “I’m not a robot” checkbox—but include hidden steps that execute harmful code. This tactic exploits users’ familiarity with real CAPTCHAs to bypass security measures. It’s often delivered via compromised legitimate sites, malicious ads, or phishing links, leading to the installation of information-stealing malware.
An example of a Fake CAPTCHA is below:

Such malware allows cybercriminals to steal passwords, browser data as well as the ability to download additional malware and remote access tools for full system control and keylogging and screen capture capabilities.
UCL Impact
ISG investigated a few incidents with the Fake CAPTCHA in 2025 in which UCL users inadvertently followed the instructions on a fake CAPTCHA page. In one instance in late October, the individual was visiting a site that they trust and were prompted to complete the fake CAPTCHA process in order to proceed to the webpage, indicating that some of the lures in this campaign are very likely targeted at the education sector.
Following successful deployment, malware would very likely be used to obtain credentials which could be used to directly access UCL systems. Such methods can be used as an access point to attempt to compromise other assets and systems within UCL’s network.
Actionable Recommendations
- Do not follow any instructions on a website to complete a CAPTCHA or other verification process which does not take place entirely within your internet browser.
- Never paste commands from websites into Run/Command Prompt.
- Ensure that you are using a modern endpoint security tool which is able to detect and block execution of malicious code on your computer.
Sources
https://www.york.ac.uk/it-services/about/news/2025/fake-captcha/
https://itservices.wp.st-andrews.ac.uk/2025/06/17/fake-captcha-scams-target-universities/
Black Friday Scam Advice
By Daniela Cooper, on 26 November 2025

If a screen reader is needed, please use the PDF version linked below:
News Roundup:
By Daniela Cooper, on 13 November 2025

A quick roundup of some information security related news. First some information on security issues involved in the Louvre Heist. Then some phishing emails that we have seen recently that resulted in some compromised accounts.
The Louvre Heist
A lot of the news surrounding the Louvre has been focused on the physical theft, the BBC has done a nice visual story on this (I’ll link to it below). However, few have mentioned that the password for the Louvre surveillance system was “LOUVRE”, the weak password that cost them £76 million. See the following articles that explain it below:
https://www.bbc.co.uk/news/resources/idt-fde5876a-c35c-48a2-b4cf-d255bd25611b
It’s a strong reminder to remember to address the basics when it comes to security.
Recent Phishing Emails
We have seen some phishing emails lately that have led to some account compromises, see image below:

In this case the tell tale signs were:
- the To address not actually being the recipients address
- unexpected link to an attachment
This looks a lot like the sort of email you might get if someone was trying to share a file from SharePoint with you. If you receive something like this that is not expected, double check with the sender, preferably not via email.
Reporting Suspicious Emails
If you receive an email that you wish to have investigated, you can take the following steps:
- Send the Email to phish@ucl.ac.uk: When you send an email to this address, it will automatically scan the email and provide you with an automated response with the result. You can also click on the “Report Phishing” or “Report Junk” buttons (instructions shown here), which will provide you with the same automated response.
- Raise it Directly with ISG: If you believe that the classification given was wrong, or you still want a security analyst to directly review the email, you can raise a ticket with ISG with the email included, which can be done here.
Cyber Security Awareness Month – Week Four
By Daniela Cooper, on 29 October 2025

Welcome to week four and the last week of Cyber Security Awareness Month. This week is all about preventing identity theft. As usual we will be running the weekly quiz to win a £25 Amazon voucher so make sure you read all the way to the end!
Preventing identity theft
How to steal an identity
It’s as easy as…
Most of the data needed to steal a person’s identity can be found online. Data can be bought (illegally) from the dark web, or found using free online tools and publicly available information.
Armed with a full set of personal details, a criminal is able to:
- Purchase products or services using the details of the victim.
- Apply for credit cards using the details of the victim.
- Create false identity documents for use in further criminal offences, such as employment fraud, benefit fraud and mortgage fraud.
- Access or open bank accounts to steal money directly or to commit money laundering offences.
Social media
Personal accounts
Social media profiles are an important part of our personal and professional identities (and an important part of staying up till 3am watching YouTube videos).
Unfortunately, criminals also use social media to ‘fill in the gaps’ when researching victims. They look for full names, dates of birth, addresses, education histories, pet names and family members.
This doesn’t mean we shouldn’t use social media. It just means we need to keep a few things in mind. Things like:
- Are you uploading photos to social media?
- Do they contain sensitive information (like details of debit cards or flight tickets)?
- Have you geotagged yourself?
- Geotagging doesn’t just let people know where you are – it lets them know where you’re not!
Professional accounts
Information posted to professional social media accounts can be used by criminals to orchestrate social engineering attacks. Before posting, consider if and how your post might be used by a criminal, either in isolation or when combined with other information.
Pro Tip
Use Google’s Manage your reputation tool to see exactly what personal information is publicly available and remove any unwanted content or associated search results.
Mobile phones
SIM swapping
Mobile phones are often used by companies as a means of authentication. You’ll be sent a code by text message as part of the login process. You need to enter the code along with your username and password to authenticate your login.
Because mobile phones are being used more and more frequently for authentication, they’re now being targeted by criminals in a process known as SIM swapping.
How’s it done?
SIM swapping sees criminals gain access to your phone by requesting a new SIM card from your network provider.
This is how:
- First, criminals contact your phone company pretending to be you.
- Next, they answer a series of security questions. If successful, they amend your address.
- Then, they request a new SIM card.
- Finally, they activate the new SIM card. Your SIM stops working and all phone calls and text messages are diverted to the criminal.
Once a criminal has access to your mobile phone, they can use it to reset passwords, log in to accounts and treat it as a means of verification when contacting companies.

Pro Tip
Protect yourself from SIM swapping by contacting your network provider and setting a password on your account. In the future, they’ll ask you for your password instead of security questions.
Bulletproof your identity
Know the signs!
The following may indicate theft:
- Unauthorised transactions made from your bank account.
- Letters or emails about products or services you do not recognise.
- Letters or emails failing to arrive.
- Phone calls and text messages suddenly cease.
- Goods delivered without being ordered.
- Credit or debit cards being declined, or refusal for credit related services.

Act fast!
If you think you are a victim of identity theft, take immediate action. Criminals will act quickly to exploit your details for maximum gain; you need to act quicker.
- If you notice unauthorised transactions or a credit/debit card is declined, contact your bank or card provider.
- If phone calls or text messages suddenly cease, contact your network provider.
- If you receive letters, emails or goods you weren’t expecting; or letters, emails or goods you were expecting fail to arrive, contact the company or provider concerned.
Long-term protection
Sign up to free credit-scoring services
Before committing identity related offences, it’s common for criminals to open free credit scoring services using their victim’s details and an illicit email address. This allows criminals to monitor their victim and know when a new credit service has been granted.
By signing up to a service first, you prevent criminals from opening shadow accounts in your name. Signing up also allows you to monitor your credit history and check for suspicious spending. In the UK, consider Equifax, Experian, and TransUnion.
Register to vote at your current address
Doing so prevents criminals from registering your details at their address so they can redirect and intercept your mail.
Remove yourself from the open voters register
Next time you vote, be sure to tick the box requesting your information be removed from the public electoral register.
Secure your mail
All the information needed to commit identity theft lies in a single bank statement. So, stealing mail is a highly effective way of committing identity theft.
Make sure your mail is secure. Shred any documents containing personal details before disposing of them.
Consider protective registration
Protective registration is a service offered in the UK by CIFAS, a non-profit fraud prevention organisation. Protective registration places a marker next to your name and personal details in the secure National Fraud Database. Companies signed up to the database take extra steps to protect details, making it harder for criminals to apply for products and services in your name.
The one downside to protective registration is it can take longer to gain approval for credit. The service costs £25 and lasts for 2 years.
Summary
1. Identity theft is the most prevalent form of cybercrime. Be vigilant. Regularly check bank statements and free credit scoring accounts.
2. Review security settings on your social media accounts. Be mindful of what you post. The internet never forgets.
3. Call your network provider and secure your mobile phone account with a password.
Week Four Quiz
For the chance to win a £25 Amazon voucher answer the following question:
Q: What are the 6 signs that may indicate identity theft?
Please send your answers to ISG via https://myservices.ucl.ac.uk/self-service/requests/new/provide_description?from=wizard&service_id=1296&service_instance_id=3679&support_domain=myservices-isg – use the subject line Cyber Security Awareness Month Quiz Entry – Week Four.
Many thanks to CybSafe for providing the content for this blog post!
Cyber Security Awareness Month – Week Three
By Daniela Cooper, on 21 October 2025

Welcome to week three of Cyber Security Awareness Month. This week is all about security incidents. If you haven’t already, take a look at the online security briefing with the City of London Police that Birkbeck have kindly invited UCL staff and students to attend. As usual we will be running the weekly quiz to win a £25 Amazon voucher so make sure you read all the way to the end!
Security incidents
It happened a few days ago. Still, Peter hadn’t told anyone.
As he was sitting in his meeting, he couldn’t stop thinking about it.
“Should I say something? People will judge me. They’ll avoid me. They’ll know.”
So Peter didn’t say a word.
Everyone at his company was affected. And most of his friends. And his friends’ friends, too.
Eventually, 10% of the world’s internet-connected computers were compromised.
What happened to Peter?
Peter received an email with the subject line ILOVEYOU. He opened the attached love letter. This started the malware’s spread.
What’s malware, you might ask?
Malware is malicious software. It’s computer code that can crash devices. It can also steal data, passwords, browsing history and money.

Malware can also lock and delete personal files – which is one of the ways the “ILOVEYOU” malware hurt Peter and its other victims.
After overwriting files, it emailed itself to everyone in Peter’s contact list.
In total, ILOVEYOU caused more than US$15 billion of damage. It left company reputations in tatters.
Bonus content: Six types of malware
Viruses – Viruses attach themselves to normal files. They run when the file is opened. Viruses rely on people sharing infected files to spread.
Worms – Worms are like viruses, but they spread without any human interaction. The most dangerous types replicate across networks. ILOVEYOU was a worm – which is how it affected so many people.
Trojans – Trojans don’t harbour bloodthirsty Ancient Greeks! But they are brutal. Trojans usually open “backdoors” into computers and networks, granting criminals remote access.
Ransomware – Ransomware is worm-like malware that restricts access to files or systems. It then demands victims pay a ransom to regain access. Paying the ransom doesn’t always overcome the infection. Access may be lost forever.
Spyware – Spyware lets criminals spy. It can track what you’re viewing and what you’re typing. Spyware can even turn on webcams and modify security settings.
Grayware – Grayware is software that sits in the “gray” area between malware and software. Think unwanted browser extensions and pop-up ads. Infections pose little direct threat, but they can trigger spontaneous fits of rage.
Was ILOVEYOU avoidable?
It’s unlikely.
But Peter knew about ILOVEYOU early. He could have slowed the spread and reduced the damage it caused.

We can all reduce the impact of malware. It starts with taking responsibility: to prevent, to detect, and to report.
Preventing
Verify emails
If you receive an unexpected email, and you are uneasy about doing something as a result, verify.
Verify by calling back the person you think the message is from. Do so using known contact details.
Check where links lead before clicking
Pro Tip
Found a suspicious site or receive a suspicious email? Report it on the NCSC website and to your IT department.
Show (and check) file extensions
Attachments can contain malware – that’s how Peter’s nightmare started. Some file types are more likely to contain malware than others.
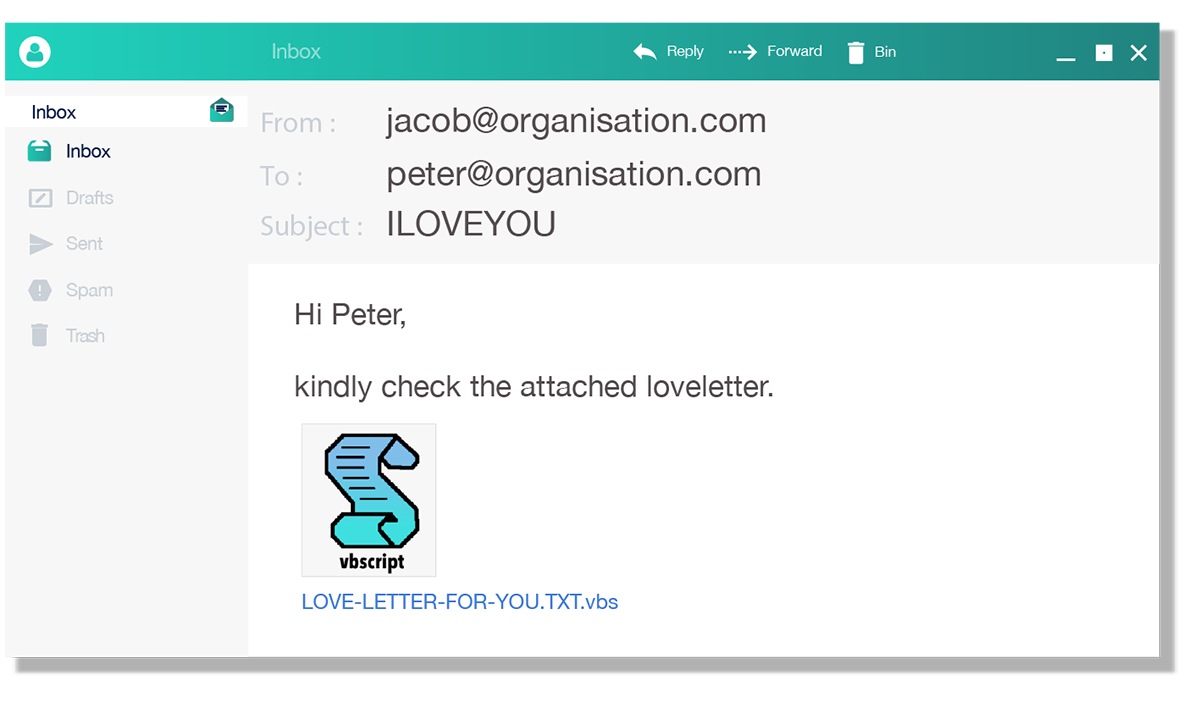
Image description
The image above is a screenshot of an email which contains an attachment with the file extension ‘.vbs’, this attachment is supposedly a love letter.
File extensions are the last three, four or five letters after a filename, like “essay.docx”.
They make dangerous files easier to spot.
File extensions aren’t always displayed by default. If you use a personal device for work, turning on the “Show file extensions” setting will help you to spot dangerous files.
What type of files are dangerous?
All files have the potential to be dangerous. Some are more dangerous than others:
Action files: Files that end with .exe, .vbs or .scr all perform actions when opened or downloaded. They often carry malware.
Macros: Macro-enabled Microsoft Office files can also contain malware. They have an ‘m’ in their file extensions, like “proposal.docm”.
Pro Tip
Microsoft Office will sometimes ask to “Enable macros” or “Turn off protected view”. Doing so can run a series of pre-programmed actions. It’s risky!
Vigilant professionals only open or interact with files they are expecting, and if they know the sender.
Ask for help if you’re ever unsure.
Bonus content: File types
More dangerous:
- Executable – .exe
- Screensaver – .scr
- Visual basic script – .vbs
- MS Word (macro-enabled) – .docxm .docm
- MS Powerpoint (macro-enabled) – .pptxm .pptm
- MS Excel (macro-enabled) – .xlsxm .xlsm
Less dangerous:
- PDF – .pdf .fdf .xfdf
- Image – .jpeg .jpg .png .gif .jp2 .jpx .tif .tiff
- Video – .avi .flv .wmv .mov .mp4
- MS Word (no macros) – .docx .doc
- MS Powerpoint (no macros) – .pptx .ppt
- MS Excel (no macros) – .xlsx .xls
Isolate devices
Malware spreads when devices connect.
Plugging unknown or unauthorised devices into work equipment increases risk. This includes charging cables, USB sticks etc. They can be adapted to carry malware, too.
Refraining from plugging in unauthorised devices – and only charging devices from power sockets – reduces risk.
Download apps safely
Malware can be hidden in useful-looking apps. The apps behave like the real thing while stealing data in the background.
Always download apps from reputable sites like the Apple app store or Google Play. Check reviews before downloading.
Work related software can be downloaded from the UCL Software Database: https://swdb.ucl.ac.uk/
Heed security warnings
Security warnings are the messages displayed by browsers before they allow access to dangerous sites.
Security warnings can be overridden. Doing so is a risk and potentially a breach of policy.
If security warnings restrict access to sites needed for work, letting someone know is the best thing to do (Line manager, IT Team or Security Team). It’s safer and, long-term, will help others in your organisation too.
Detecting
The following can be signs of malware infection:
- People report receiving spam from your email address.
- New icons appear on your desktop or in your web browser.
- Pop-ups appear or programs start running on their own.
- Messages tell you an unknown program is trying to access the internet.
- Your device is unusually slow or crashes at random intervals.
A special mention: Ransomware
Ransomware is worm-like malware that restricts access to files or systems. It then demands victims pay a ransom to regain access. Paying the ransom doesn’t always overcome the infection. Access may be lost forever.
It’s the most destructive and prolific form of malware.
If a device has been infected with ransomware, you’ll likely see a message similar to this:
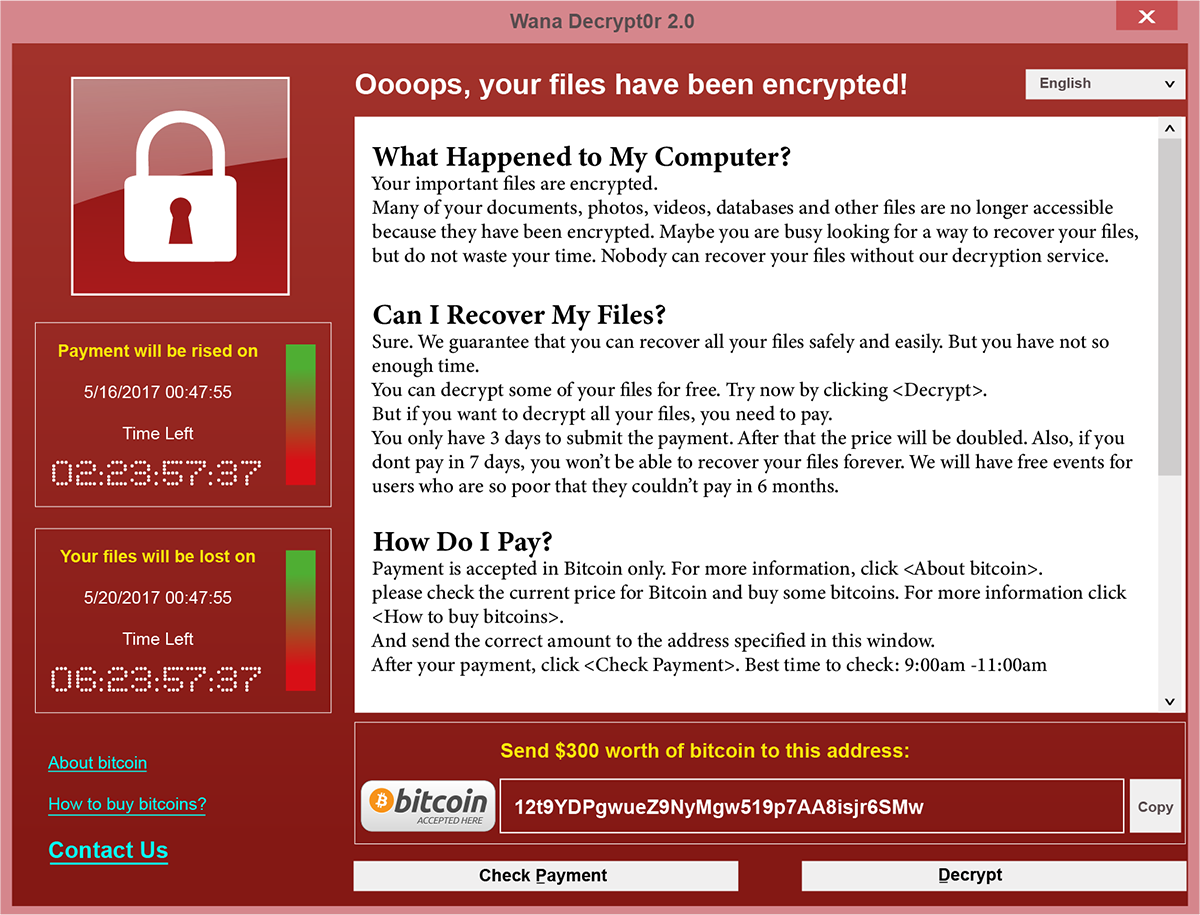
Image description
A large red pop-up containing a ransom note
If you do see a message like this, acting quickly is your chance to make a difference.
Reporting
Reporting security incidents protects organisations from criminals. Still, not all security incidents are reported.
Often it’s because people feel responsible, like Peter. Peter chose not to report so as not to bring attention to himself.
It’s okay to make mistakes. It’s not okay to hide them.
In reality, reporting a security incident is more like a “good catch”. Something happens. You notice it. You report it. Good catch.
Security related incidents should be reported to the UCL Information Security Group via https://myservices.ucl.ac.uk/
Birkbeck security briefing with the City of London Police
Birkbeck have kindly invited UCL staff and students to attend a Cyber Security Baseline Knowledge Briefing via Teams that they are running with the City of London Police. Registration for the event is here: https://events.teams.microsoft.com/event/b87c79fd-ec1c-4ea3-808f-4e551cc7a7f8@89d07f47-d258-463c-8700-635ffaeca38e
Registrations from UCL email addresses only.
Week Three Quiz
For the chance to win a £25 Amazon voucher answer the following question:
Q: Who should you report a UCL related security incident to?
Please send your answers to ISG via https://myservices.ucl.ac.uk/self-service/requests/new/provide_description?from=wizard&service_id=1296&service_instance_id=3679&support_domain=myservices-isg – use the subject line Cyber Security Awareness Month Quiz Entry – Week Three.
Thanks to CybSafe for providing the content for this blog post!
Cyber Security Awareness Month – Week Two
By Daniela Cooper, on 15 October 2025

Welcome to week two of Cyber Security Awareness Month. This week is all about spotting fake emails. Also take a look at the online security briefing with the City of London Police that Birkbeck have kindly invited UCL staff and students to attend. As usual we will be running the weekly quiz to win a £25 Amazon voucher so make sure you read all the way to the end!
Spotting fake emails
One slow day, whilst sitting in his office, James Linton noticed something. Emails don’t show the sending email address by default. He realised he could put any name there he wanted.
So he did, for five months.
He started by pranking his colleagues. He sent them emails that looked like they were from their CEO. He loved the excitement and wanted more.
James’ first real victim was the CEO of a large British bank. James sent him an email purportedly from the bank’s chairman. Suspecting nothing, the CEO engaged in an exchange praising the chairman.
James leaked the email exchange, embarrassing the CEO and prompting the bank to reconfigure their email systems. SINON_REBORN – James’ prankster alter ego – had arrived!
The pranking spree continued.
The Governor of the Bank of England.
And the White House!
Sending fake emails was exhilarating. James compared the excitement of it to the high of gambling –“You fire out three emails, and one of them comes up. When it does, you realise you have one on the line.”
James’ emails worked. Over and over again.
They worked because they won his victims’ trust.
That’s exactly what targeted fake emails do.
What are fake emails?
Fake emails look like they’re from legitimate or known sources, like a person or company you know.
These days, fake emails are difficult to spot.
The idea that most fake emails come from “long-lost relatives” is a myth. Today’s fake emails are more convincing. For the most part, they’re free from spelling and grammatical errors.

Fake emails can be either generic or targeted.
Generic fake emails are low in complexity but high in volume. Criminals send out millions of them. They usually look like they’re from a well-known company, like Apple or Amazon.
Targeted fake emails are harder to recognise and are increasingly common. They’re unique to the recipient and usually reference information found on platforms like LinkedIn.
Pro Tip
You may have heard some people refer to fake emails as “phishing”. They’re exactly the same thing. Targeted fake emails are sometimes called “spear-phishing”.
Creating legitimate-looking fake emails isn’t as hard as you might think.
How did James Linton create fake emails?
James decided on his target first. Then he picked his character based on his target’s professional and personal connections.
The next step was to find a hook. The hook was usually an interest both James’ target and character shared.
James then created a fake email address using his character’s name.
Finally, James added extra credibility to his fake emails. For example, he might hand type a second “email” below his message. This additional text, James believed, made his emails seem as though they had been forwarded.
James also favoured adding “Sent from my iPhone” to the end of messages. This made it seem like his messages were sent by an ordinary person, not “somebody huddled over a laptop in their hoodie.”
Pro Tip
How to create legitimate-looking fake emails
A guide by James Linton:
1. Pick your target.
2. Pick your character.
3. Create a hook.
4. Create a fake email address.
5. Add extra credibility.
Ian Levy: a target too far
After tricking the White House, James’ search for worthy prey continued. That was when he landed on the Technical Director of the UK’s National Cyber Security Centre (NCSC) – Dr Ian Levy.
Posing as a colleague – the Director of Operations – James “accidentally forwarded” an email from another colleague – the Director of Communications – to Ian, including a link to an article.
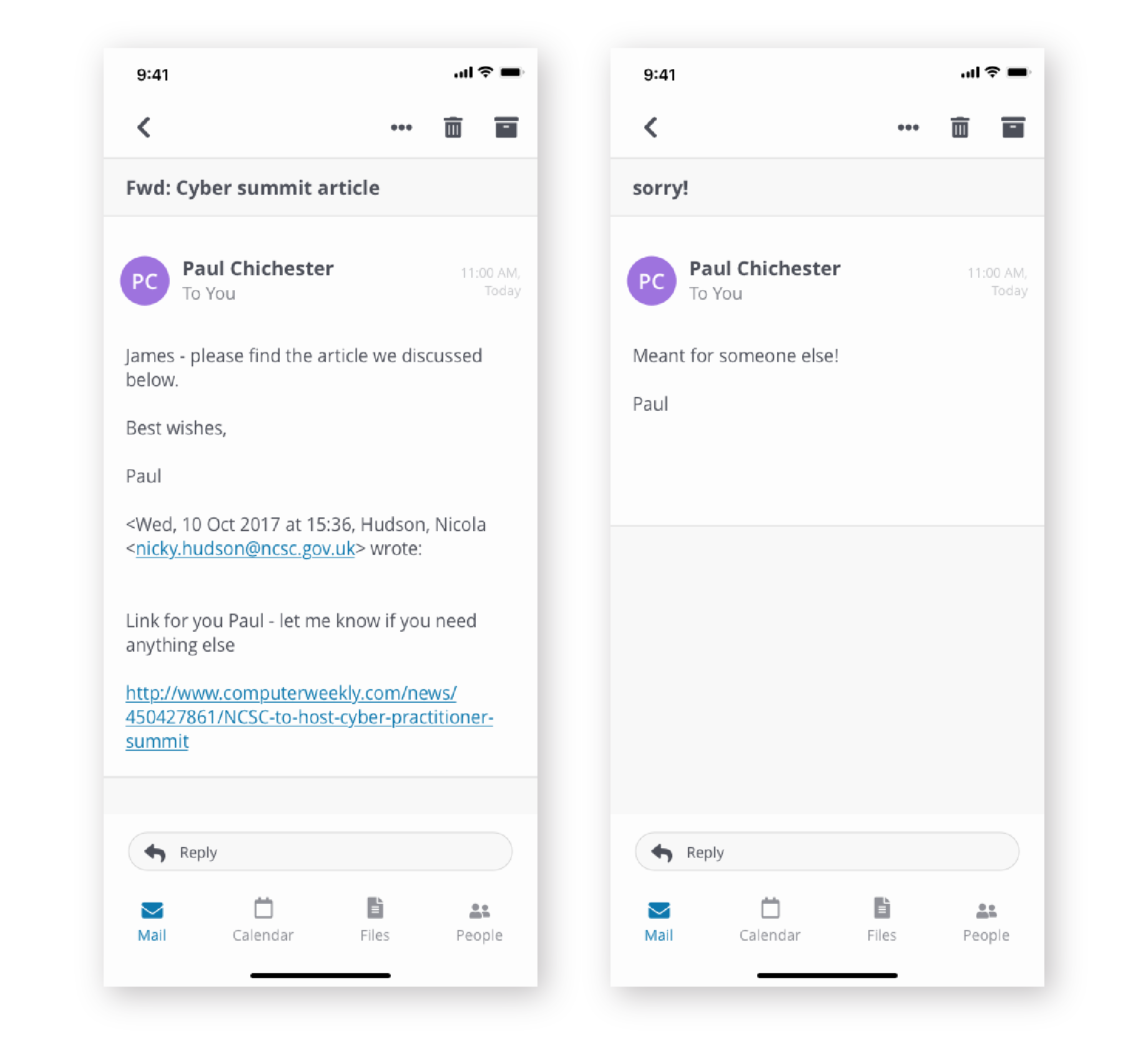
After inspecting the link on this phone (by a good old “touch-and-hold”), Ian suspected the emails were fake.
How to spot fake emails
You can use Ian Levy’s 3-step checklist:
Pro Tip
How to spot fake emails
1. Check sender’s address.
2. Check content.
3. Check links or attachments.
Step 1: Check sender’s address
Email inboxes show sender names, but they don’t always show addresses.
You can click on the sender’s name to reveal their actual email address. Pay attention to the information that comes after @.
Right after Ian had noticed the link protection of mail.com – instead of ncsc.gov.uk – he examined the sender’s address:
paul.chichester.ncsc.gov@mail.com
It didn’t look right. It was supposed to end with @gov.uk. He was intrigued, so he played along, humoring his adversary. Eventually, Ian Levy convinced James Linton to reveal his identity.
Pro Tip
Do you recognise the sender or the sender’s email address?
- Click on the sender’s name to reveal the email address.
- Contact the person you think the email is from – using anything but that email address.
Step 2: Check content
Fake emails use emotional manipulation to trick people. Notice the different types of emotions evoked:
Panic
Make a payment – your manager needs you to make an urgent payment.
Worry
Verify some information – someone has tried to access a company or service you rely on (such as a bank, phone provider or TV service).
Curiosity
Open an attachment – you’ve been sent a confidential document to read.
This is how James Linton attempted to trick Ian Levy. The emails “accidentally forwarded” from his colleague evoked curiosity.
Kindness
Visit a website – a colleague needs you to visit a website to check the content and provide your opinion.
Trust
Provide sensitive information – a colleague needs you to reveal sensitive information to help them with a task.
Pro Tip
Is the email unexpected? Does it convey an undue sense of urgency? Does it ask you to break policy?
- Slow down and think.
- Check the sender details.
- Call the person you think the email is from and ask them. Call them using a known contact number.
Step 3: Check links or attachments
Links can be displayed in their raw format (www.google.com) or as a hyperlink (this). They can also be disguised or shortened, like this https://bit.ly/3yJanNJ.
To see the true destination of a link, hover your mouse over it.
Or, if on your phone, do what Ian did. Touch & hold the link to reveal its true destination. This is how Ian noticed the link for mail.com, instead of ncsc.gov.uk.
File extensions – the last 3 or 4 letters after the dot [.] at the end of the file – tell you what a file does. So make sure you inspect them before opening attachments.
Pro Tip
Does the email include a link or attachment you don’t recognise?
- Hover your mouse over a link to see its true destination.
- If you are using Google Chrome, the browser has a built-in safe browsing feature that will show a warning before taking you to a dangerous site – keep an eye out for these warning messages.
- You could also use a reliable URL scanner to check whether or not a link is safe to open.
Bonus content: File extensions
Files ending .exe, .vbs and .scr are more likely to be dangerous. If you see a file that contains any of these extensions, especially if what you think you are opening is meant to be a read only file, such as a document, photo or video, be cautious.
Enable “Show file extensions” on your computer as it allows you to check file types before opening them.
Make sure the file you think you’re opening is what it claims to be:
- PDF – .pdf .fdf .xfdf
- MS Word – .docx .doc
- MS PowerPoint – .pptx .ppt
- MS Excel – .xlsx .xls
- Image – .jpeg .jpg .jp2 .jpx .png .gif .tif .tiff
- Video – .avi .flv .wmv .mov .mp4
Can you spot fake emails?
Below are four emails – see if you can spot the fake ones.
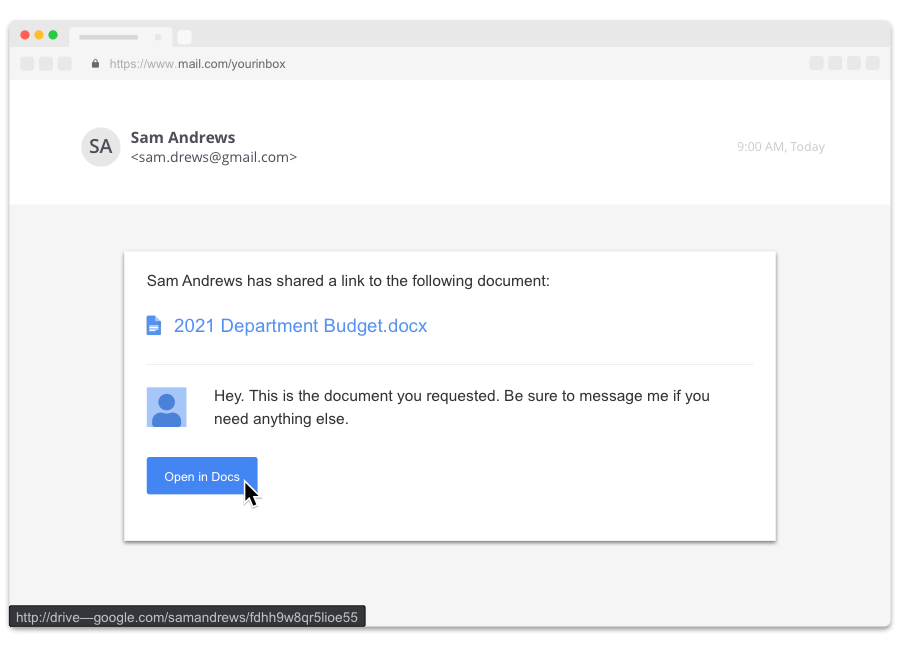
Real or fake?
Fake!
Check links or attachments.
Hovering over “Open in Docs” shows you its true destination, a look-alike link – http://drive—google.com/samandrews/fdhh9w8qr5lioe55.
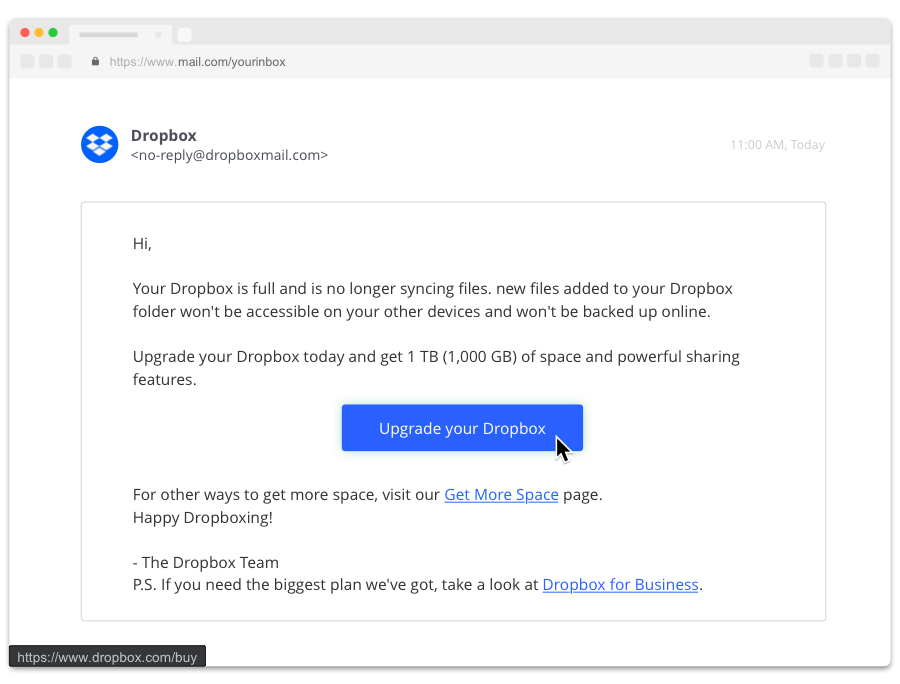
Real or fake?
Real!
This is a legitimate Dropbox email.
Check the sender’s address.
The sender is “dropboxmail.com” – although this looks unusual, a quick search reveals it’s legitimate.
Check links or attachments.
The link is to a secure site https://www.dropbox.com.
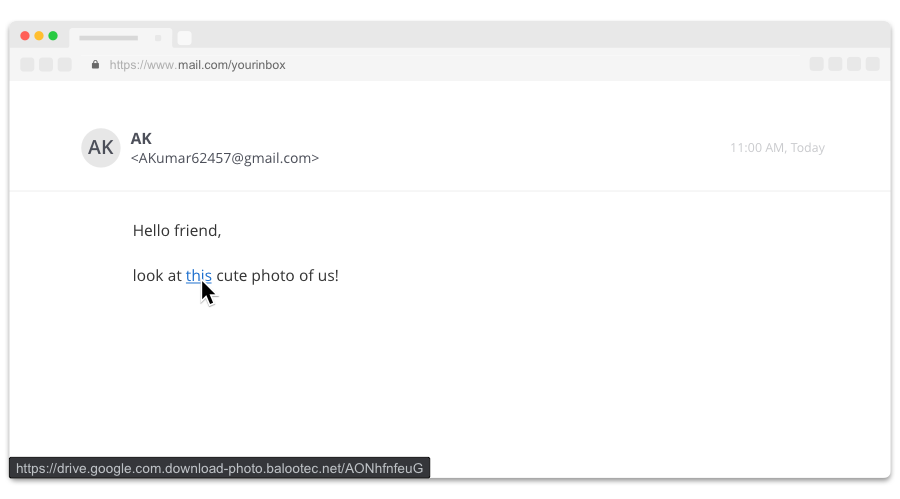
Real or fake?
Fake!
Check links or attachments.
Hovering over “this” shows you the link’s true destination – a look-alike website address https://drive.google.com.download-photo.balootec.net/AONhfnfeuG. The real address is “balootec.net” which is disguised to look like Google Drive.
Check the sender’s address.
Do you know AK? Clicking on the sender’s name reveals their actual email address. Does the email address “AKumar62457@gmail.com” seem familiar?
Check content.
Is the email unexpected? What emotions does it evoke? Someone addressing you as “friend” and sending you a “cute photo” likely evokes curiosity.
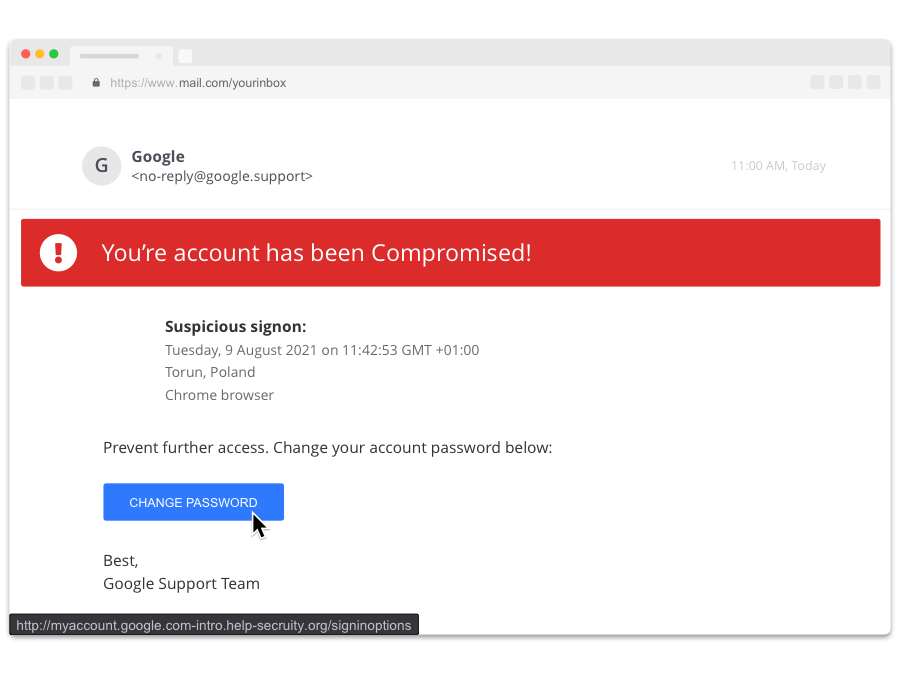
Real or fake?
Fake!
Check links or attachments.
Hovering over “CHANGE PASSWORD” shows you its true destination – http://myaccount.google.com-intro.help-secruity.org/signinoptions. The link actually points to the website of “help-secruity.org”, not Google.
And “secruity” in the link is misspelled.
Check the sender’s address.
Clicking on the sender’s name reveals their actual email address. The sender address “google.support” isn’t actually used.
Check content.
The email contains poor grammar – “You’re account” and “Suspicious signon”.
Summary
After Ian Levy coaxed James Linton out of hiding, the pair teamed up. They co-authored a blog about their experience.
Their aim was to help people spot future fake emails.
After completing this module, you’ll have everything you need to do just that.
How to spot fake emails
1. Check the sender’s address. Click on the sender’s name to reveal it. Contact the person you think the email is from using a known contact number.
2. Check the content of the email. Is the email unexpected? Is it asking you to do something unusual? What emotions does it evoke?
3. Check links or attachments. Hover over them to see their true destination. If they look suspicious, search for verifiable online information.
Birkbeck security briefing with the City of London Police
Birkbeck have kindly invited UCL staff and students to attend a Cyber Security Baseline Knowledge Briefing via Teams that they are running with the City of London Police. Registration for the event is here: https://events.teams.microsoft.com/event/b87c79fd-ec1c-4ea3-808f-4e551cc7a7f8@89d07f47-d258-463c-8700-635ffaeca38e
Registrations from UCL email addresses only.
Week Two Quiz
For the chance to win a £25 Amazon voucher answer the following question:
Q: What are the three steps to spotting a fake email?
Please send your answers to ISG via https://myservices.ucl.ac.uk/self-service/requests/new/provide_description?from=wizard&service_id=1296&service_instance_id=3679&support_domain=myservices-isg – use the subject line Cyber Security Awareness Month Quiz Entry – Week Two.
Thanks to CybSafe for providing the content for this blog post!
Securely using Microsoft Teams
By Peter Andrews-Briscoe, on 8 October 2025
Microsoft Teams is now an integral part of working life. Most staff at UCL will use it daily; meetings, chats, file sharing, and project updates all flow through it. But as with any tool, how we use it matters. While Teams makes work more efficient, careless practices can put sensitive data at risk. We have received reports recently of sensitive data being shared inadvertently with users, which has caused security and reputational concerns.
This article outlines the main security concerns with Teams, and the best practices we can all adopt to keep our work safe.
Common Security Concerns in Teams
- Meeting Recordings and Transcripts
- The risk: Recordings and transcripts are automatically shared with all meeting invitees – even those who didn’t attend. This can unintentionally expose sensitive information to the wrong people.
- What to do:
- Think before recording. Only record what it is necessary to record.
- If you do record, review and manage access afterwards. Remove unintended invitees from the sharing list, alongside invitees who were only present briefly.
- Use private meetings for highly confidential topics.
- Do not use any third-party transcription services that are not approved by UCL (for example, UCL’s approved transcription provider is CoPilot because the information stays in the UCL tenet).
- Guest Access
- The risk: External guests (consultants, external speakers, suppliers) may have more visibility in Teams than intended, depending on how channels and permissions are configured.
- What to do:
- Check whether guests are present (or have access to the chat or recording) before sharing sensitive files or screens.
- Use dedicated channels/teams for external collaboration instead of mixing internal and external staff.
- Chat Messages
- The risk: Chats can feel informal, but they are retained and discoverable. Oversharing in chat can create a lasting record of sensitive data.
- What to do:
- Keep chats professional and work-related.
- Avoid sharing personal data, passwords, or confidential project details in chat. Use secure storage for sensitive files.
- File Sharing
- The risk: Files shared in Teams may inherit broader permissions than expected (e.g., shared to “everyone in the team”).
- What to do:
- Double-check permissions before uploading sensitive files.
- Use SharePoint or OneDrive links with restricted access where appropriate.
- Screen Sharing
- The risk: Accidentally displaying sensitive information (emails, personal data, other open documents) while screen sharing.
- What to do:
- Share individual windows instead of your entire screen when possible.
- Close unrelated apps and documents before a meeting.
Best Practices for Secure Use of Teams
- Pause before you share: Whether it’s your screen, a file, or a recording, consider if the information is suitable for everyone present.
- Review recording settings: Disable auto-recording unless it’s absolutely necessary.
- Be mindful of attendees: Always check the participant list before discussing sensitive topics.
- Practice “need to know”: Not every conversation needs to involve the whole team or go into the record.
Microsoft Teams is a powerful tool – but it requires good judgment to use. The platform makes it easy to share information widely, but that convenience is also the risk. The best defence is awareness: pause, check, and make sure only appropriate information is shared.
By working with Teams responsibly, we can protect sensitive information while still benefiting from everything the platform offers.
Cyber Security Awareness Month – Week One
By Daniela Cooper, on 7 October 2025
It’s already October and with October comes another Cyber Security Awareness Month. We will be releasing a post each week with a different security topic to remind us of the importance of information security in both our work and home lives. This week is all about Passphrases and MFA. As usual we will be running the weekly quiz to win a £25 Amazon voucher so make sure you read all the way to the end!
Passphrases and MFA
I was sipping my latte when I overheard her.
“It was a bargain! Only $700 at xyz-style.com!! Just look how cute it is!!!”
The dress is alright… Judith Harris. That’s her full name. A glance at her employee ID was all I needed.
Judith is clearly well-off. Who else describes a $700 dress as “a bargain”?
So what’s next?
I start looking online to see what other personal information I can find.
It takes just a few minutes.
Her Facebook and LinkedIn accounts are both public. In a few minutes, I know a lot about her: date of birth; home and work email address; family members; recent holidays; hobbies; and the dog’s name, obviously.
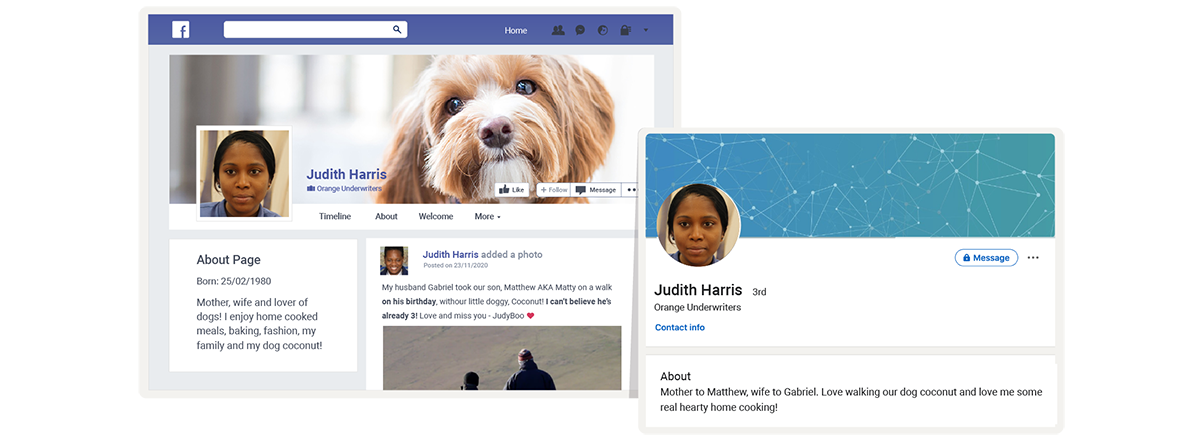
I bet I can use the information to break into her email account. From there I can access other accounts and services linked to it, like PayPal, Amazon, and her credit cards.
To start, I’ll need to crack her password. To do this I need a “wordlist”. A wordlist is just a file containing passwords. Hundreds of thousands of them.
You can download generic wordlists online. In my experience though, they don’t work as well as ones you build yourself.
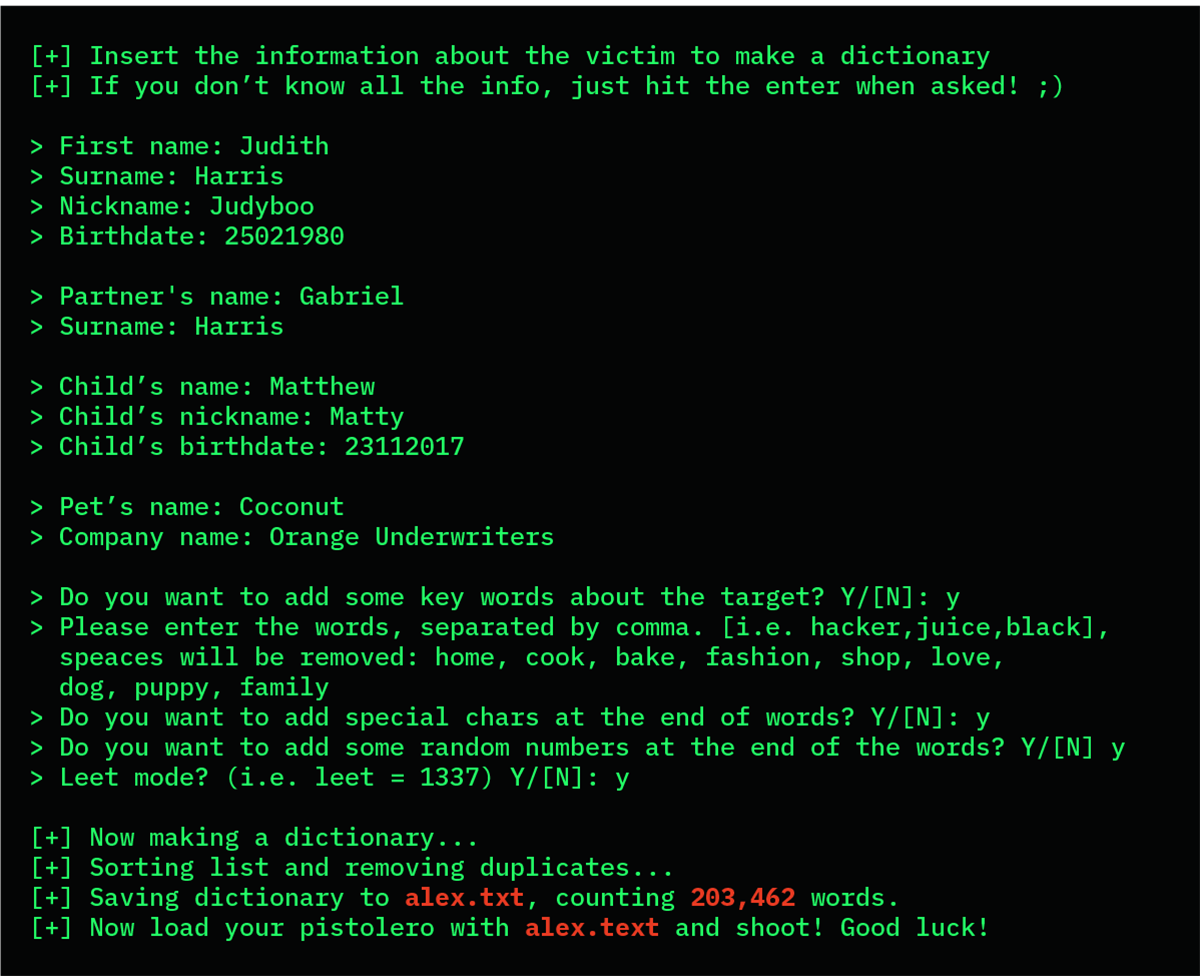
I use a piece of software called CUPP (short for Common User Passwords Profiler). CUPP generates a custom wordlist using the information I know about Judith.
This is what it looks like, if you’re interested.
There are other ways to hack accounts.
I chose to crack Judith’s password. It’s not the most effective way to hack an account. But it keeps my skills sharp. It’s also fun!
The dark web: It’s easier to buy stolen account details from the dark web. People rarely use different passwords for different accounts. I take the details from one stolen account, and use them to access other accounts belonging to the same person. It’s child’s play.
Public Wi-Fi: Public Wi-Fi is also a helpful friend. Shared networks, like the ones in coffee shops, can be used to intercept passwords.
Personally, I never use public Wi-Fi to do things I wouldn’t want other people to see, like access accounts containing personal info, send emails, or make payments. You shouldn’t either.
Fake emails, messages & phone calls: If I get stuck, or if I’m going after a cautious individual, I’ll reach out directly. My message will look similar to something they’d normally receive, like a delivery notification or a message from a colleague.
The message will contain a link to a fake website that looks genuine. The website will be set up to steal their password. These “sophisticated attacks” are great at tricking people into giving away their passphrases.
Right, I have Judith’s email address and 203,462 potential passwords. But I can’t just bang on Gmail’s front door. Google will lock the account if the wrong password is entered too many times.
What about xyz-style.com…? The website she got her “bargain” of a dress from. I wonder if it has the same security controls in place.
…bingo! I’m in.
(I say “bingo” as if it happened instantly. It didn’t. It took about 8 minutes. Had to get another coffee and everything.)
Scared now, huh? No need to be.
People don’t realise they can check if passwords or account details have been leaked online. haveibeenpwned.com is a website that lets you check if you have an account that has been compromised in a data breach. It’s owned by Troy Hunt. Troy is a respected security professional and Regional Director at Microsoft.
Check it out: haveibeenpwned.com
It can be scary, but it’s worth doing. You can also sign up to an alerts system which will notify you if your details appear in future breaches.
Back to Judith.
I’m in to xyz-style.com. There’s not much to see. The site doesn’t store card details, unfortunately.
Doesn’t matter. The reason I hacked into xyz-style.com was to attribute a password to Judith. People frequently reuse passwords. Let’s try the same one to login into her email account…
Forget about passwords.
In the past, you may have been advised to use a complex password. Something like this…
~2EnQ4#t?
It’s bad advice.
Complex passwords are very difficult for humans to remember. They’re also very easy for computers to guess, or “crack”.
Something like the above would take just 8 days for a computer to crack.
Using personal information in your passwords is also a bad idea.
So what should you do?
Use a passphrase.
Passphrases are similar to passwords. They’re just stronger and easier to remember.
Pro Tip
An easy way to set a passphrase is to use three random words, or a simple but memorable saying, for example:
- linguini pencil london
- dogs eat meat dogs play beats
Join the words together to create your passphrase.
You can include special characters, CAPITAL LETTERS and numbers.
Place them in simple, memorable positions, like at the end:
- linguiniPENCILlondon2020!!
- DOGSeatmeatDOGSplaybeats2020!!
Your passphrase should be at least 14 characters long, but longer is better, if you can.
Extra protection.
…It works!
I’ve hacked into Judith’s email. She’s made it so easy for me.
You might be wondering what the value of this exercise is. Let me show you.
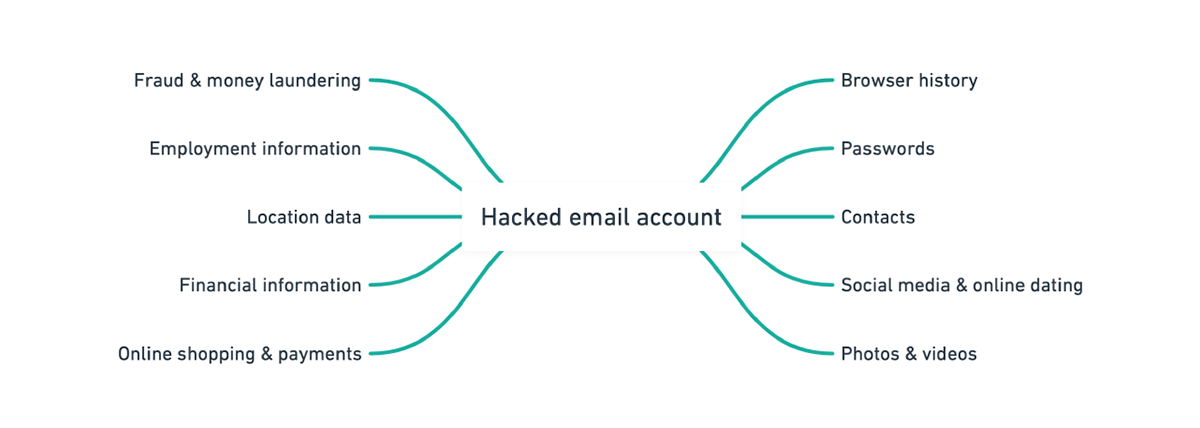
Many people do not realise how much they have invested in their email accounts until those accounts are in the hands of criminals.
In nearly all cases, the person in control of an email address can reset the password of any associated service or account.
By then it’s too late.
Stealing, cracking or buying passphrases is challenging. But it’s not impossible.
I’d suggest using extra measures to protect your accounts. That’s what I do.
Step 1: Protect your valuable accounts with multi-factor authentication (MFA)
MFA is a powerful tool to protect your main email and other high-value accounts. It takes an account from about 50% secure to 99% secure.

MFA lets you verify your identity twice when logging in, using your passphrase and a unique code from your phone.
This means if I have access to your passphrase, I cannot get into your account unless I also have access to your phone.
Many believe you have to enter MFA codes every time you login. You don’t! After logging in for the first time, the device and the account become “linked”. Once the device is linked, it’ll usually log in automatically. Easy.
Setting up MFA
Step 2: Use biometric readers
Biometric readers are things like fingerprint scanners and facial recognition cameras. They bolster the effectiveness of your passphrases.
Biometric readers are a real time saver. But they’re only as strong as the passphrase they represent. If you have access to, say, a fingerprint scanner, only use it in conjunction with a strong passphrase!

The four-digit pin you’ve “protected” your phone with? That’s not secure even with a biometric reader. You can do better!
Step 3: Use a password manager
A password manager stores all your passwords (or passphrases) in one place. They’re great if you have lots of different passwords to remember.
The passwords stored in the password manager are secured with one “primary passphrase”.
You can get them as standalone apps or you can use the one in your web browser. Both are good.
If you don’t feel comfortable using a password manager, you can write passwords down. Store them somewhere safe, out of sight and, most importantly, away from your computer.
Summary
I’m not real, obviously.
I serve a purpose though. I represent real people.
I am online criminals, nation-state hackers, and every person who doesn’t have a job or means to make money legally. If you make it easy for me, I will eventually get you.
I do this because I can. And because people make it easy for me
1. Using strong passphrases is the most effective thing you can do to prevent cyber crime.
2. Use a strong and separate passphrase for your most valuable accounts, like your home and work email accounts.
3. MFA takes an account from about 50% secure to 99% secure. If it’s available, use it!
4. If you’re struggling to remember multiple passwords, consider a password manager.
Week One Quiz
For the chance to win a £25 Amazon voucher answer the following question:
Q: What is the recommended minimum number of characters for a passphrase?
Please send your answers to ISG via https://myservices.ucl.ac.uk/self-service/requests/new/provide_description?from=wizard&service_id=1296&service_instance_id=3679&support_domain=myservices-isg – use the subject line Cyber Security Awareness Month Quiz Entry – Week One.
Thanks to CybSafe for providing the content for this blog post!
Call for nominations: UCL Cyber Security and Data Protection Awards 2025
By Daniela Cooper, on 30 April 2025
Do you know someone who deserves recognition for their support in making UCL a more secure place to study and work? If you do, please nominate them for a UCL Cyber Security and Data Protection Award.
The awards recognise the above and beyond work that our staff and students do to help keep UCL safe and secure.
Award Categories:
- Above and Beyond Award – An individual who has gone out of their way to be helpful or proactive in a cyber security activity.
- Keeping UCL Safe Award – An individual who has made a difference to the cyber safety of UCL.
- Departmental Award for good security citizenship – An individual who has been a good cyber security citizen and role model.
- Data Protection Award – An individual who has gone above and beyond to develop how UCL protects personal data.
- Annual CISO Research Collaboration Award – For the academic or researcher who has done exceptional work in bridging the research to practitioner gap.
How to make a nomination:
Please contact the UCL Information Security Group to make a nomination: MyServices. Include your reasons for nominating and the category.
The deadline for submissions is the 23rd May.
The awards ceremony will take place as part of the UCL Cyber Security and Data Protection showcase event in June. This is an invite only event, award winners will be contacted in advance with an invitation for the event.
 Close
Close


