Fake CAPTCHA Phishing Attacks
By Peter Andrews-Briscoe, on 2 December 2025
Written by Bassit Mayet
Summary
During 2025, there were reports from different reputable sources of an increase in the use of fake CAPTCHA verification pages to trick users into downloading and running malicious code.
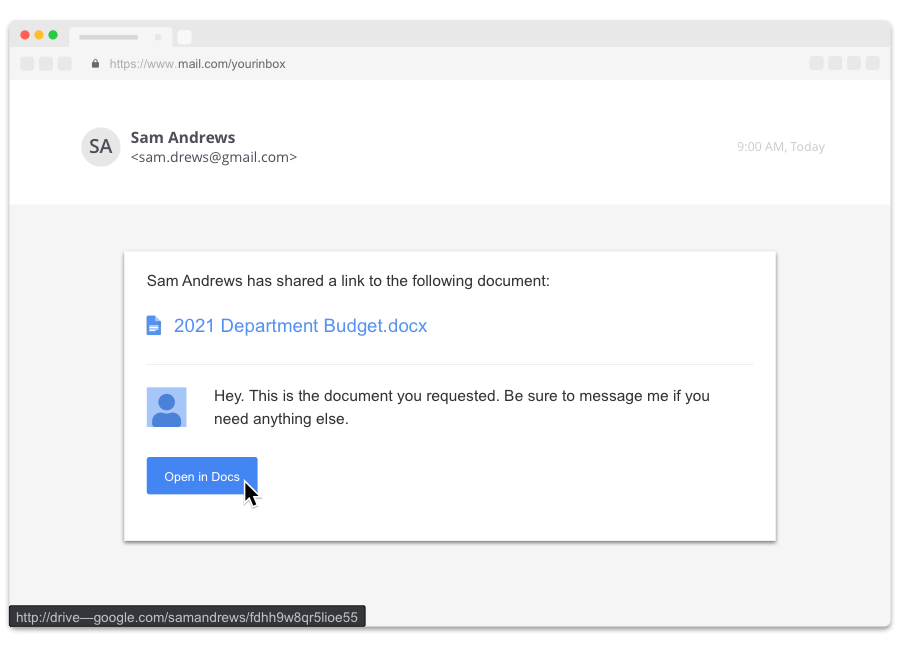
Fake CAPTCHA malware refers to a social engineering scam where cybercriminals create deceptive CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) challenges on websites to trick users into self-infecting their devices with malicious software. These fake CAPTCHAs mimic legitimate ones—such as the “I’m not a robot” checkbox—but include hidden steps that execute harmful code. This tactic exploits users’ familiarity with real CAPTCHAs to bypass security measures. It’s often delivered via compromised legitimate sites, malicious ads, or phishing links, leading to the installation of information-stealing malware.
An example of a Fake CAPTCHA is below:

Such malware allows cybercriminals to steal passwords, browser data as well as the ability to download additional malware and remote access tools for full system control and keylogging and screen capture capabilities.
UCL Impact
ISG investigated a few incidents with the Fake CAPTCHA in 2025 in which UCL users inadvertently followed the instructions on a fake CAPTCHA page. In one instance in late October, the individual was visiting a site that they trust and were prompted to complete the fake CAPTCHA process in order to proceed to the webpage, indicating that some of the lures in this campaign are very likely targeted at the education sector.
Following successful deployment, malware would very likely be used to obtain credentials which could be used to directly access UCL systems. Such methods can be used as an access point to attempt to compromise other assets and systems within UCL’s network.
Actionable Recommendations
- Do not follow any instructions on a website to complete a CAPTCHA or other verification process which does not take place entirely within your internet browser.
- Never paste commands from websites into Run/Command Prompt.
- Ensure that you are using a modern endpoint security tool which is able to detect and block execution of malicious code on your computer.
Sources
https://www.york.ac.uk/it-services/about/news/2025/fake-captcha/
https://itservices.wp.st-andrews.ac.uk/2025/06/17/fake-captcha-scams-target-universities/
 Close
Close