Cyber Security Awareness Month – Week Three (Part Two)
By Daniela Cooper, on 18 October 2024

Here is Part Two of Week Three’s content for Cyber Security Awareness Month. This short security related story is all about Sophisticated Attacks. If you haven’t already entered the Week Three (and Week One and Week Two) quizzes to win a £25 Amazon voucher, see the details on how to enter at the bottom of the post.
Sophisticated attacks
Meet Sophie. Sophie is a security consultant. She gets paid to think like a criminal and break into buildings.
Organisations hire Sophie to test their security.
Sophie uses fake emails, phone calls and text messages to pretend to be someone she’s not. Much of the time, she approaches people in person and manipulates them to help her.
Sophie’s attacks are “sophisticated” because she targets individuals. Sophisticated attacks work by getting people to do things they wouldn’t usually do, like provide access to restricted information or areas, pay “invoices”, or break policy.
Sophisticated attacks are often called “social engineering” attacks.
Recently, a client hired Sophie to test two of their facilities: a manufacturing plant and a nearby office.
This is how she did it…
Stage 1: Research
Your social media accounts are Sophie’s best friend. The more information you share, the more options you give her.
Sophie has several fake profiles. You might even be connected to one. (A good reason to always verify who people are before accepting requests.)
Sophie started by using one of her accounts to look for people who worked at the facilities. She found a Facebook account of a young woman, “Mary”.
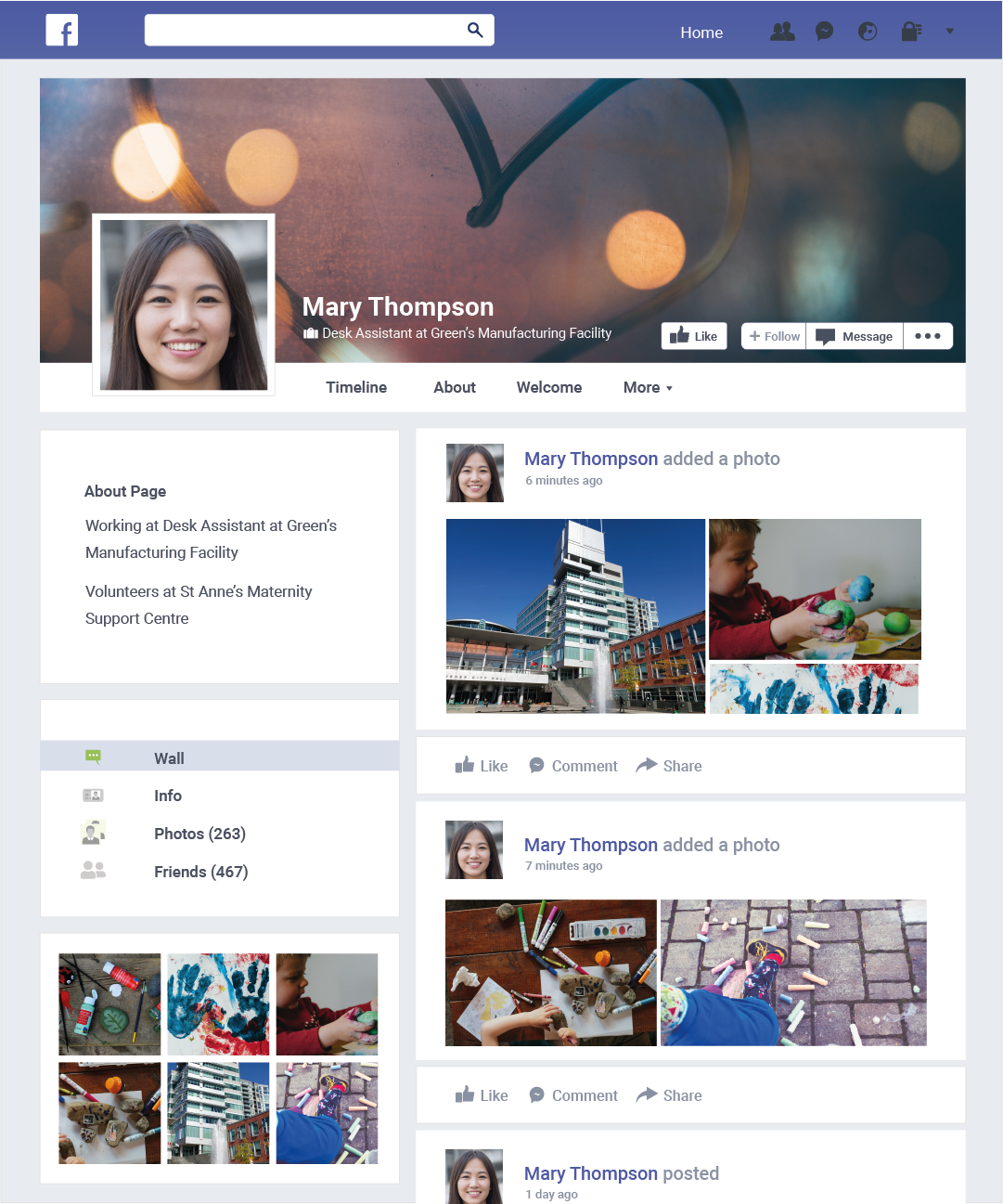
Mary worked as a front desk assistant at the manufacturing facility.
Mary’s Facebook profile showed pictures of her volunteering at a maternity support centre. Sophie could tell Mary cared for children and new mothers. Of course, she would use this to her advantage.
Stage 2: Setting the scene
Sophie knew she would more likely be welcomed into the facility if staff were expecting her. So, she went about setting the scene for her arrival.
Armed with the knowledge about Mary, Sophie picked up the phone.
Before dialling, Sophie disguised her phone number so it looked like she was calling from head office. This process is known as “spoofing”.
Spoofing: When emails, phone calls and text messages are made to look like they’re from someone else.
By spoofing her client’s head office phone number, Sophie added credibility to her attack. Spoofing works because people don’t always verify who they’re talking to.
Pro Tip
What to look out for: Phone calls
All phone numbers can be faked. This includes internal extensions.
Criminals pose as legitimate people, like bank staff or IT teams. Their aim is to convince targets to do things they wouldn’t usually do.
Control your emotions, especially if the caller tries to get you to panic, worry, or act under pressure. Don’t do things you wouldn’t normally do. Stick to policy.
When necessary, verify. Call back using a known contact number (either that you know or that’s published online).
What to look out for: Text messages
Criminals also use fake text messages to encourage people to:
- Click links that lead to fake websites. Fake websites are set up to steal personal details or install malware.
- Call numbers that connect to criminals, or premium-rate lines.
Fake text messages can even drop into ongoing conversation threads with genuine contacts!
It’s rare for us to advise never to do something. Text messages are the exception. There’s no way to determine the real sender of a text message, so:
- Never click links in texts.
- Never follow directions sent via text.
- Don’t do things you wouldn’t normally do. Stick to policy.
- Verify if you need to, search online for legitimate details.
All suspected fake phone calls and text messages should be reported.
“Hi Mary! My name is Barbara.”
Sophie got right to it. She explained she was “Barbara”, a project coordinator arranging the refurbishment of company offices.
Sophie told Mary she was sending an interior designer out the next day. The interior designer, Sophie said, was putting together a facility-update proposal.
Mary was cautious, “Well, that’s great! But why the short notice?”
It was time for Sophie to play her trump card.

All phone numbers can be faked. This includes internal extensions.
Sophie explained she should have called sooner. But she was overloaded with work and was due to give birth in six weeks, “If my boss finds out I messed this up he’s going to flip.”
Mary cut her off. “Oh, it’s ok. We’ll work this out! Tell me about the baby! Is it your first? Boy or girl?!”
Mary was hooked. She was a good person, who just wanted to help.
The two talked babies and birth plans for a while. Mary then took down the name of the designer who would visit the next day, “Claire”.
If only Mary had verified who she was talking to. If only she had hung up and called back.
But she didn’t…
Stage 3: Attack
Sophie showed up the next day as “Claire” the interior designer. Claire had her own business cards and website! (Sophie had made them the night before.)
Mary and her boss were waiting to welcome Sophie. She shook hands and handed them each a business card. Mary gave Sophie a visitor badge and invited her in.

Sophie gained rapport with the staff by asking them what they wanted from an office space. “You want a standing desk? New chairs over here?! Ergonomic keyboards for all!!”
Everyone was very excited.
Sophie took forever looking around. Eventually Mary and her colleagues had to get back to work. They left Sophie, giving her complete, unaccompanied access to both facilities.
The company had a policy of escorting visitors. But because Sophie had been seen with trusted insiders, no one questioned her. She was free to do as she pleased.
Pro Tip
What to look out for: In-person approaches
In-person approaches rely on our desire to help. This shouldn’t be discouraged.
We should trust the people around us, but we also need to be comfortable checking if something doesn’t look or feel right.
Procedure is well thought out. It’s there to support and protect. A genuine person without ID won’t be annoyed or angry if you politely ask who they are and why they’re in the building. Trust, but verify.
What to look out for: Shoulder surfing
“Shoulder surfers” are opportunists who check screens or listen to private conversations.
When working in a shared space:
- keep your desk clear to prevent loss of physical assets,
- and consider who’s around before discussing sensitive topics.
Just like you would be with your PIN at an ATM, or whilst on the phone to your bank.
A privacy screen is a thin piece of plastic that’s placed over your monitor. It stops people seeing what’s on your screen.
What to look out for: Fake USB devices
Fake USB devices are USB devices that damage or steal data from computers or networks.
Any USB device can be harmful. This includes charging cables.
Labels like “bonus payments” can make USBs enticing. Letting curiosity take over can be risky.
Report any stray USB devices you find. Plugging them in isn’t worth it.
Sophie took her time. She gained network access and stole several thousand dollars worth of computer equipment.
Once she’d finished, Sophie found the office of the person who’d hired her…
“Who?…. Wait, what? How? How did you get in here?!”
Sophie sat down and smiled, “Let me start from the beginning…”
Summary
Everyone should be able to do their job without worrying about sophisticated attacks.
Trust those around you. But recognise when you’re being steered by emotions. Be comfortable checking when things aren’t right.
Don’t panic if you accidentally click, say, or do something unwise in an odd moment. It’s okay as long as it’s reported. Reporting buys time. It prevents further damage.
Stopping sophisticated attacks: “Trust, but verify”
1. All emails, phone calls and text messages can be made to seem as if they’re from someone else.
2. If you receive a request you weren’t expecting, or one that has an undue sense of urgency, slow down. Verify and follow policy.
3. If you think you’ve identified a sophisticated attack, report it. Reporting prevents cyber crime.
“Sophie” is a real person. Her story was adapted from the original published on vice.com on 20th October 2017.
Week Three Quiz
For the chance to win a £25 Amazon voucher answer the following question:
Q: Not doing what, is like leaving the front door unlocked for criminals?
Hint: The answer can be found in the Week Three (Part One) blog post – see below.
Please send your answers to ISG via https://myservices.ucl.ac.uk/self-service/requests/new/provide_description?from=wizard&service_id=1296&service_instance_id=3679&support_domain=myservices-isg – use the subject line Cyber Security Awareness Month Quiz Entry – Week Three.
If you haven’t entered the Week One quiz yet, you can find that here: https://blogs.ucl.ac.uk/infosec/2024/10/03/cyber-security-awareness-month-week-one-part-1/
If you haven’t entered the Week Two quiz yet, you can find that here: https://blogs.ucl.ac.uk/infosec/2024/10/10/cyber-security-awareness-month-week-two-part-one/
Cyber Security Awareness Month – Week Three (Part One)
If you haven’t already read Week Three (Part One), you can find that here: https://blogs.ucl.ac.uk/infosec/2024/10/18/cyber-security-awareness-month-week-three-part-one/
 Close
Close


