Cyber Security Awareness Month – Week Three (Part One)
By Daniela Cooper, on 18 October 2024

Here is Part One of Week Three’s content for Cyber Security Awareness Month. This short security related story is all about Working Remotely. Make sure you read all the way to the end to enter our week three quiz to win a £25 Amazon voucher. If you haven’t already entered the Week One and Week Two quizzes, see the details on how to enter at the bottom of the post.
Working remotely
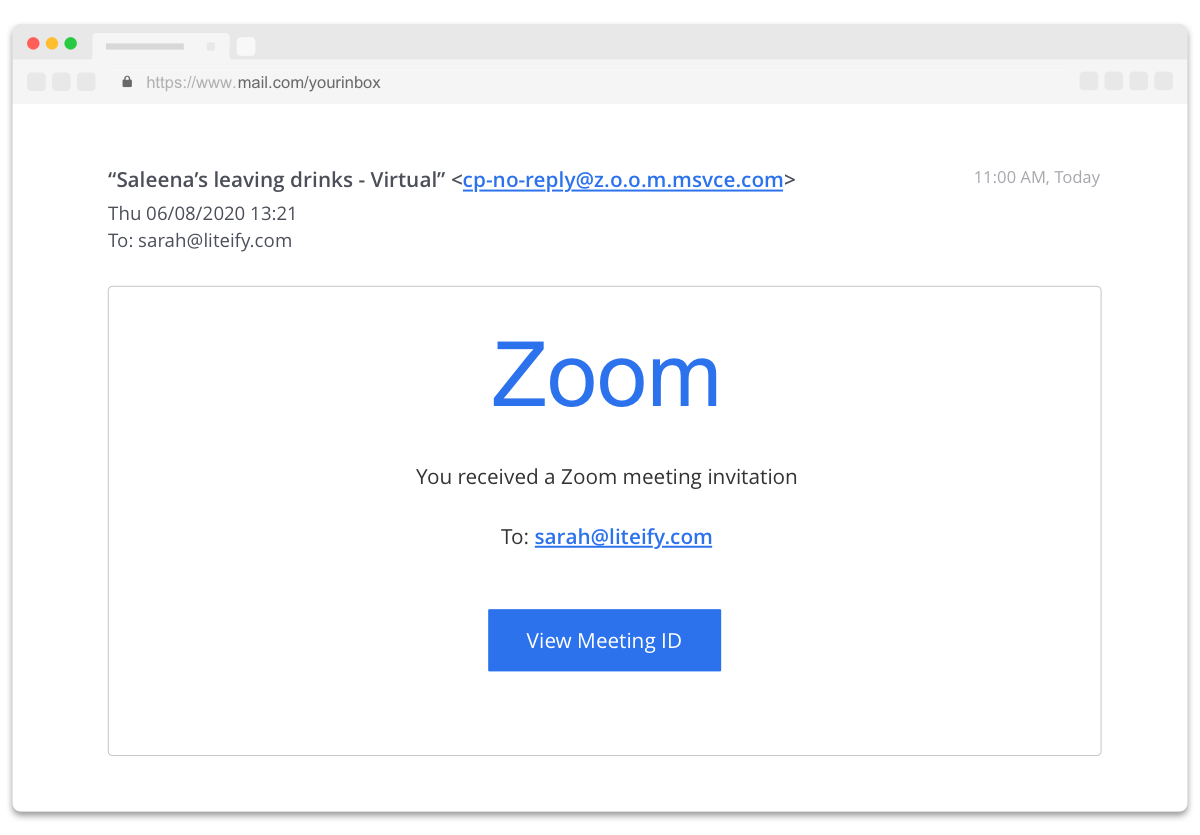
“Invite to Saleena’s virtual leaving drinks? Awesome. It’s not like there’s anything else to do!”
Sarah has been working remotely for nearly a year.
At first, she enjoyed her new environment. Cool home-office gadgets, cosy blankets, and a fresh obsession with plants.
The novelty quickly turned frustrating. No distractions, no water-cooler chats, no social interaction.
Like most people, Sarah’s desire for social interaction skyrocketed.
So, Sarah enthusiastically clicked on the Zoom invite for Saleena’s event!
Before she had a chance to read the details, the doorbell sounded. She rushed to open the door for a delivery.
By the time she came back, the invite had disappeared, and the computer had turned off.
Strange.
Where did Sarah go wrong?
Checking emails
Whether it’s the desire to feel connected or the anticipation of a precious delivery, criminals take advantage.
Unsurprisingly, fake emails more than doubled when working remotely became the new normal.
And the invite for Saleena’s leaving drinks was indeed a fake email with a fake link to a fake Zoom event. All communications can be faked to make it look like they’re from someone else.
Pro Tip
Check sender’s email address. Do you recognise it? Does it match the name of who the email is from? If not, verify using an alternative contact method.Check email content. Is the email unexpected? Is it too good to be true? If something doesn’t feel right, slow down and report it to your IT department.Check links and attachments. Do you recognise them? Hover your mouse over a link to see its true destination. Use a reliable search engine to check whether it’s safe to open.If you suspect an email, report it to your IT department or security team.You can also report it to the NCSC.
Policies, procedure, guidance, winning
Approved technology, whether it’s hardware (e.g. a work device) or software (e.g. antivirus) is set up to have the best protection possible.
By clicking the fake Zoom link, Sarah unknowingly downloaded malicious software onto her personal computer. She didn’t have the same protection in place on her own device as on the one given to her by Liteify, her organisation.
Pro Tip
Work devices often have a lot of security layers in place. If you can, make sure your work and personal devices are separate. Keep work emails on work accounts and personal emails on personal accounts. Avoid forwarding emails from one to the other, just in case.
Personal devices: Updates
If you’ve been allowed to work on a personal device, make sure you have the following protections in place.
Antivirus
Antivirus protects devices from malware and viruses. It checks links, files, software and applications against known threats and monitors suspicious activity from programs running on your device.
As with any product or service, make sure to review several options before purchasing and only buy from reputable sources. It may be that your organisation recommends, uses, or is partnered with, a chosen provider.
Check first, as you might be able to gain access to a reputable provider for free!
Updates
Not installing software updates is like leaving the front door unlocked for criminals.
Outdated devices or apps can be an entry point for malware into home networks. Updates keep them secure by fixing newly discovered vulnerabilities.
Enable auto-updates for as many other pieces of software as you can.
Firewalls
A firewall is a set of virtual rules that tell the computer what data to let in, let out, and keep out. Here is how to turn it on
After restarting her device, Sarah noticed nothing wrong with it. She had no idea about the malware, until she got a strange email from a colleague.
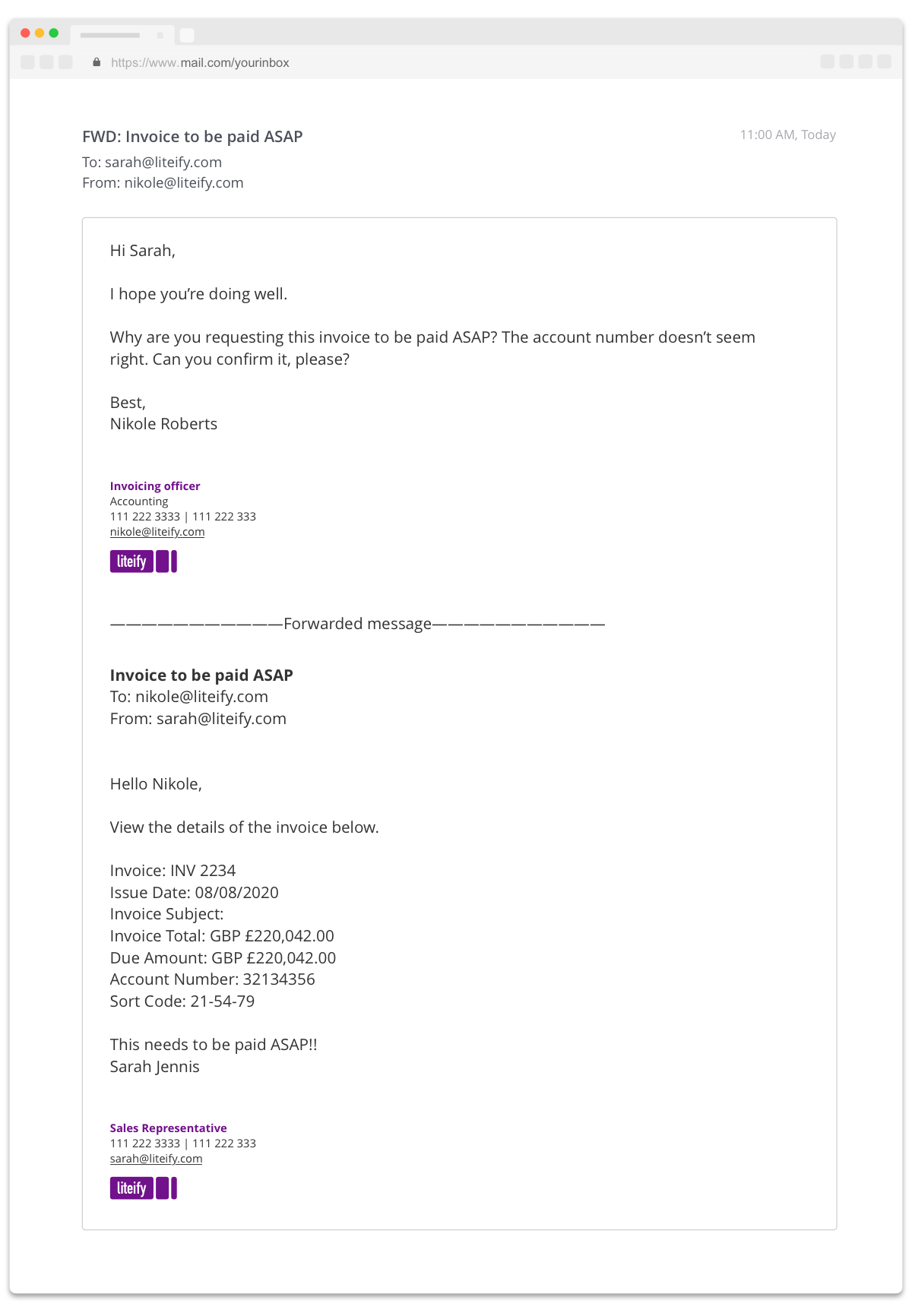
She definitely did not send that email. After a short panic, Sarah reported the suspicious email she purportedly sent to her colleague.
Other colleagues had reported the unusual emails from Sarah, too. Thanks to these reports, the company’s security team successfully identified the fake email that attackers used to infiltrate Liteify’s systems and hijack Sarah’s email account.
Routers and passphrases
Though she felt uneasy and embarrassed, Sarah was also relieved. She understood the impact an accidental click and the absence of antivirus could have and decided to take action.
Routers
Unsecured routers can put both personal and work devices at risk.
Wi-Fi networks can be vulnerable if the default router settings aren’t changed as it makes it easy for criminals to gain remote access.
Secure your home routers for protection when working from home.
Strong and separate passphrases
Securing home routers is only effective if they’re protected with strong passphrases. Stronger and easier to remember, passphrases are passwords but better!
Reusing passphrases is risky. Using unique passphrases for each account is one of the easiest ways to protect your accounts in the event of a data breach.
Pro Tip
The most effective action to prevent cyber crime on a personal level is to use strong and separate passphrases on valuable accounts and home routers. If the systems or policy allow, use separate passphrases on workplace accounts.
How to – passphrases
An easy way to set a passphrase is to use three random words, such as:
workHOMEsecure2022
Join the words together to create your passphrase. You can include special characters, capital letters and numbers in memorable positions, like at the end:
workHOMEsecure2022!!
Passphrases should be at least 12 characters long – but the longer, the better.
Working from anywhere
Just like Sarah, 1 out of every 2 people worldwide work remotely at least once a week. Whether working from a beach in Bali or a local coffee shop, there are additional things to consider when working away from home.
Public Wi-Fi
Public Wi-Fi hotspots can be used to monitor web use and intercept personal information. You can protect yourself by tethering or using a VPN.
Tethering is sharing a device’s (phones, most often) internet connection with another device.
VPNs can be downloaded as an app which creates a secure connection to the Wi-Fi hotspot.
Being aware of your environment
- Lock unattended devices to prevent unauthorised access, especially when living with others or working in a shared space.
- Use privacy screens if needed.
- Avoid discussing sensitive work topics in public.
Week Three Quiz
For the chance to win a £25 Amazon voucher answer the following question:
Q: Not doing what, is like leaving the front door unlocked for criminals?
Please send your answers to ISG via https://myservices.ucl.ac.uk/self-service/requests/new/provide_description?from=wizard&service_id=1296&service_instance_id=3679&support_domain=myservices-isg – use the subject line Cyber Security Awareness Month Quiz Entry – Week Three.
If you haven’t entered the Week One quiz yet, you can find that here: https://blogs.ucl.ac.uk/infosec/2024/10/03/cyber-security-awareness-month-week-one-part-1/
If you haven’t entered the Week Two quiz yet, you can find that here: https://blogs.ucl.ac.uk/infosec/2024/10/10/cyber-security-awareness-month-week-two-part-one/
 Close
Close


