Cyber Security Awareness Month – Week Two (Part Two)
By Daniela Cooper, on 11 October 2024

Here is Part Two of Week Two’s content for Cyber Security Awareness Month. This short security related story is all about passphrases and MFA. If you haven’t already entered the Week Two quiz to win a £25 Amazon voucher, see the details on how to enter at the bottom of the post.
Passphrases and MFA
I was sipping my latte when I overheard her.
“It was a bargain! Only $700 at xyz-style.com!! Just look how cute it is!!!”
The dress is alright… Judith Harris. That’s her full name. A glance at her employee ID was all I needed.
Judith is clearly well-off. Who else describes a $700 dress as “a bargain”?
So what’s next?
I start looking online to see what other personal information I can find.
It takes just a few minutes.
Her Facebook and LinkedIn accounts are both public. In a few minutes, I know a lot about her: date of birth; home and work email address; family members; recent holidays; hobbies; and the dog’s name, obviously.
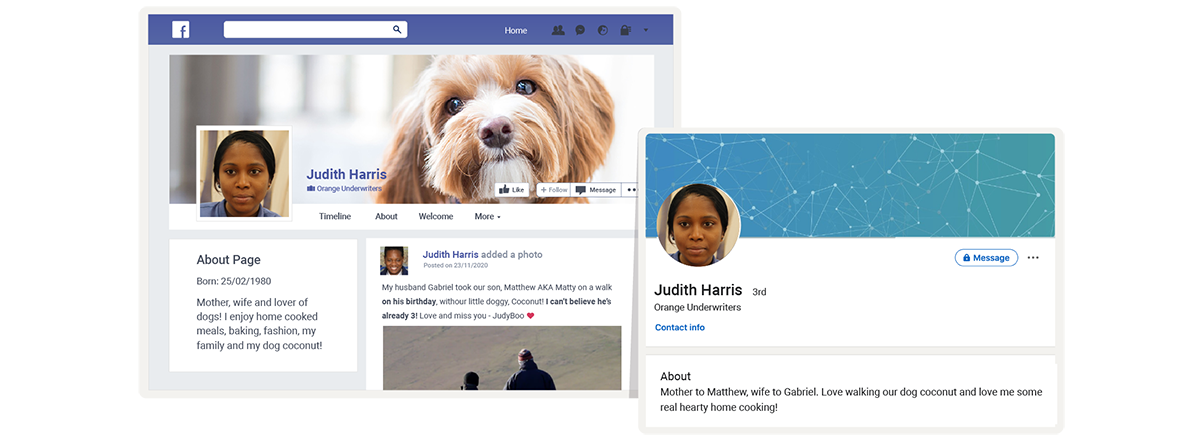
I bet I can use the information to break into her email account. From there I can access other accounts and services linked to it, like PayPal, Amazon, and her credit cards.
To start, I’ll need to crack her password. To do this I need a “wordlist”. A wordlist is just a file containing passwords. Hundreds of thousands of them.
You can download generic wordlists online. In my experience though, they don’t work as well as ones you build yourself.
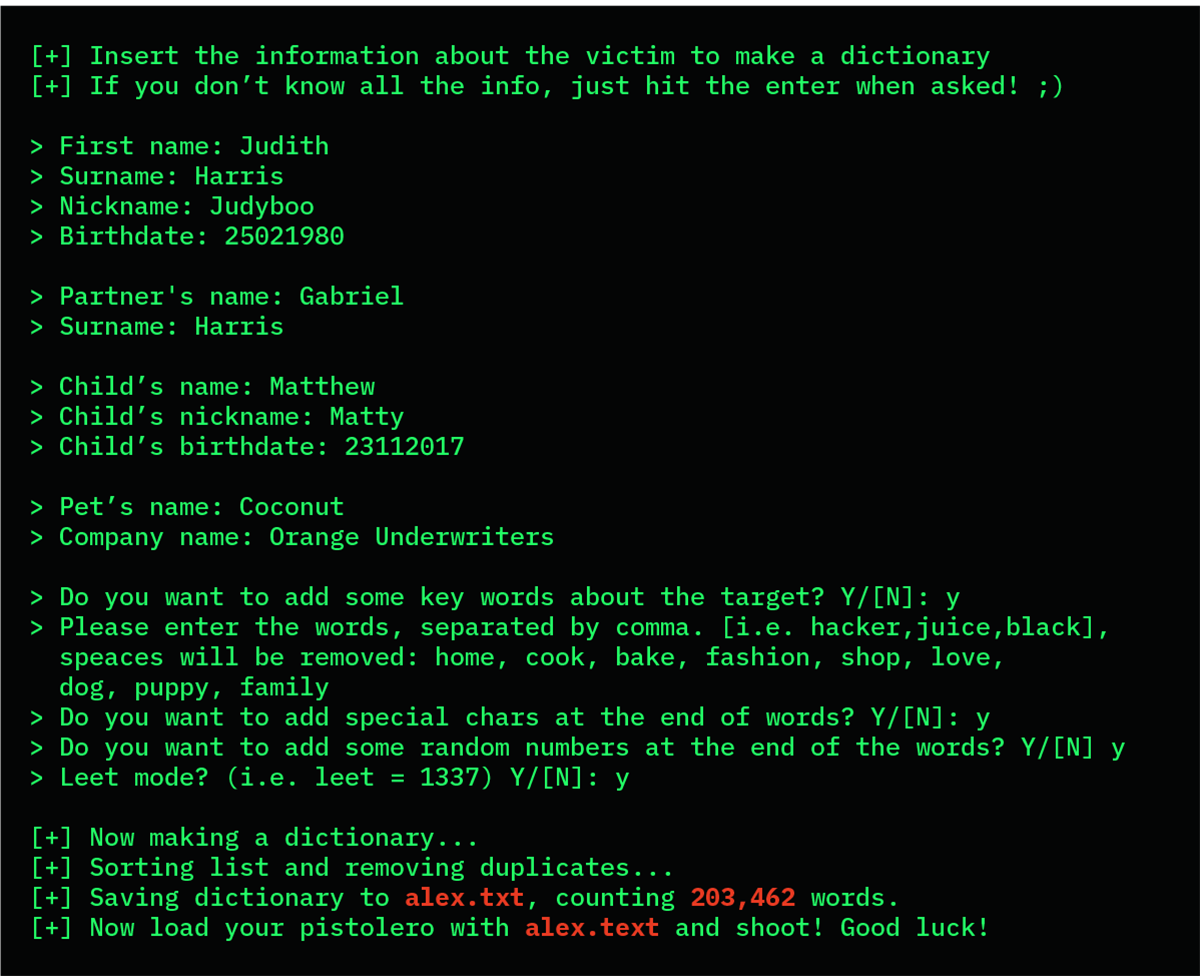
I use a piece of software called CUPP (short for Common User Passwords Profiler). CUPP generates a custom wordlist using the information I know about Judith.
This is what it looks like, if you’re interested.
There are other ways to hack accounts.
I chose to crack Judith’s password. It’s not the most effective way to hack an account. But it keeps my skills sharp. It’s also fun!
The dark web: It’s easier to buy stolen account details from the dark web. People rarely use different passwords for different accounts. I take the details from one stolen account, and use them to access other accounts belonging to the same person. It’s child’s play.
Public Wi-Fi: Public Wi-Fi is also a helpful friend. Shared networks, like the ones in coffee shops, can be used to intercept passwords.
Personally, I never use public Wi-Fi to do things I wouldn’t want other people to see, like access accounts containing personal info, send emails, or make payments. You shouldn’t either.
Fake emails, messages & phone calls: If I get stuck, or if I’m going after a cautious individual, I’ll reach out directly. My message will look similar to something they’d normally receive, like a delivery notification or a message from a colleague.
The message will contain a link to a fake website that looks genuine. The website will be set up to steal their password. These “sophisticated attacks” are great at tricking people into giving away their passphrases.
Right, I have Judith’s email address and 203,462 potential passwords. But I can’t just bang on Gmail’s front door. Google will lock the account if the wrong password is entered too many times.
What about xyz-style.com…? The website she got her “bargain” of a dress from. I wonder if it has the same security controls in place.
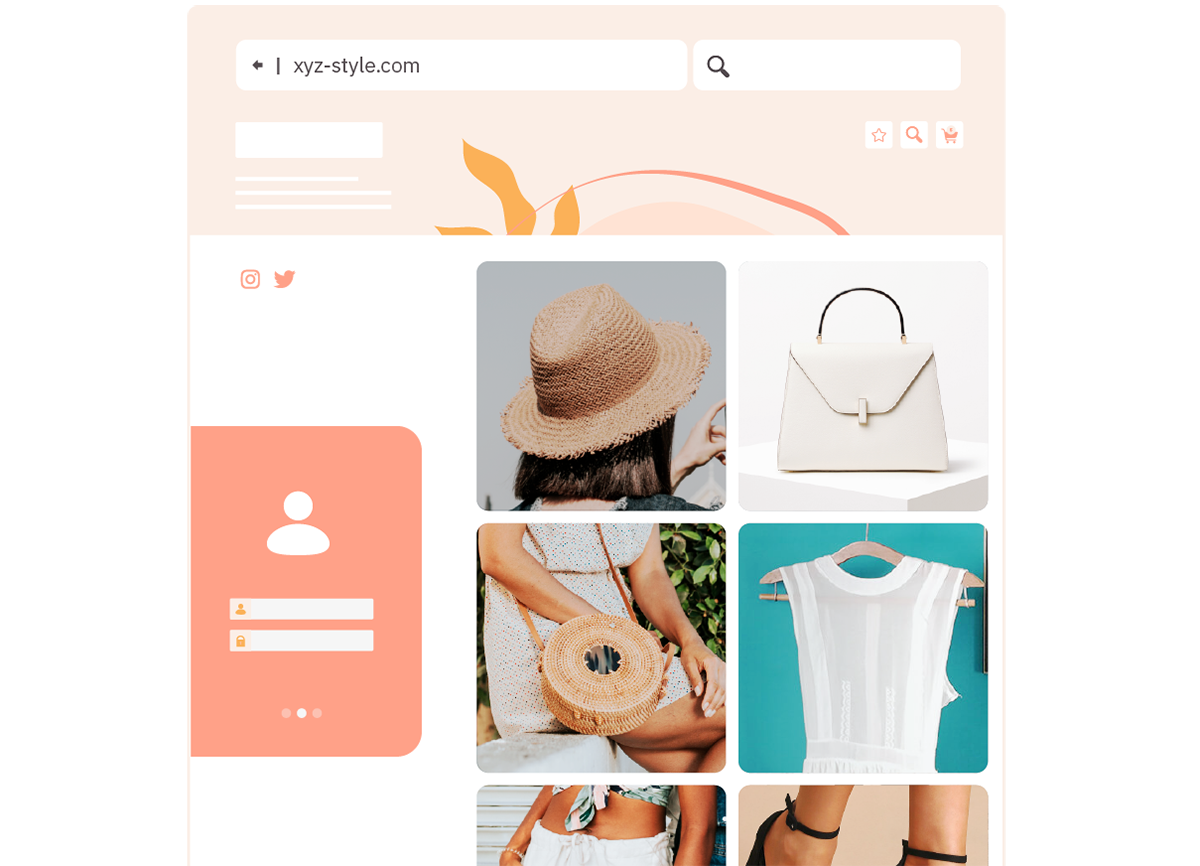
…bingo! I’m in.
(I say “bingo” as if it happened instantly. It didn’t. It took about 8 minutes. Had to get another coffee and everything.)
Scared now, huh? No need to be.
People don’t realise they can check if passwords or account details have been leaked online. haveibeenpwned.com is a website that lets you check if you have an account that has been compromised in a data breach. It’s owned by Troy Hunt. Troy is a respected security professional and Regional Director at Microsoft.
Check it out: haveibeenpwned.com
It can be scary, but it’s worth doing. You can also sign up to an alerts system which will notify you if your details appear in future breaches.
Back to Judith.
I’m in to xyz-style.com. There’s not much to see. The site doesn’t store card details, unfortunately.
Doesn’t matter. The reason I hacked into xyz-style.com was to attribute a password to Judith. People frequently reuse passwords. Let’s try the same one to login into her email account…
Forget about passwords.
In the past, you may have been advised to use a complex password. Something like this…
~2EnQ4#t?
It’s bad advice.
Complex passwords are very difficult for humans to remember. They’re also very easy for computers to guess, or “crack”.
Something like the above would take just 8 days for a computer to crack.
Using personal information in your passwords is also a bad idea.
So what should you do?
Use a passphrase.
Passphrases are similar to passwords. They’re just stronger and easier to remember.
Pro Tip
An easy way to set a passphrase is to use three random words, or a simple but memorable saying, for example:
- linguini pencil london
- dogs eat meat dogs play beats
Join the words together to create your passphrase.
You can include special characters, CAPITAL LETTERS and numbers.
Place them in simple, memorable positions, like at the end:
- linguiniPENCILlondon2020!!
- DOGSeatmeatDOGSplaybeats2020!!
Your passphrase should be at least 12 characters long, but longer is better, if you can.
Extra protection.
…It works!
I’ve hacked into Judith’s email. She’s made it so easy for me.
You might be wondering what the value of this exercise is. Let me show you.
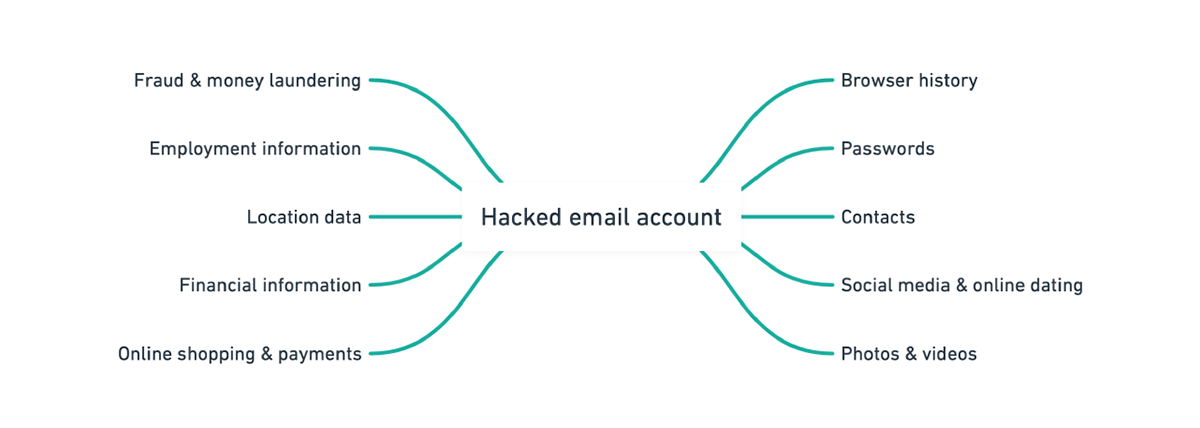
Many people do not realise how much they have invested in their email accounts until those accounts are in the hands of criminals.
In nearly all cases, the person in control of an email address can reset the password of any associated service or account.
By then it’s too late.
Stealing, cracking or buying passphrases is challenging. But it’s not impossible.
I’d suggest using extra measures to protect your accounts. That’s what I do.
Step 1: Protect your valuable accounts with multi-factor authentication (MFA)
MFA is a powerful tool to protect your main email and other high-value accounts. It takes an account from about 50% secure to 99% secure.

MFA lets you verify your identity twice when logging in, using your passphrase and a unique code from your phone.
This means if I have access to your passphrase, I cannot get into your account unless I also have access to your phone.
Many believe you have to enter MFA codes every time you login. You don’t! After logging in for the first time, the device and the account become “linked”. Once the device is linked, it’ll usually log in automatically. Easy.
Setting up MFA
Step 2: Use biometric readers
Biometric readers are things like fingerprint scanners and facial recognition cameras. They bolster the effectiveness of your passphrases.
Biometric readers are a real time saver. But they’re only as strong as the passphrase they represent. If you have access to, say, a fingerprint scanner, only use it in conjunction with a strong passphrase!

The four-digit pin you’ve “protected” your phone with? That’s not secure even with a biometric reader. You can do better!
Step 3: Use a password manager
A password manager stores all your passwords (or passphrases) in one place. They’re great if you have lots of different passwords to remember.
The passwords stored in the password manager are secured with one “primary passphrase”.
You can get them as standalone apps or you can use the one in your web browser. Both are good.
If you don’t feel comfortable using a password manager, you can write passwords down. Store them somewhere safe, out of sight and, most importantly, away from your computer.
Summary
I’m not real, obviously.
I serve a purpose though. I represent real people.
I am online criminals, nation-state hackers, and every person who doesn’t have a job or means to make money legally. If you make it easy for me, I will eventually get you.
I do this because I can. And because people make it easy for me
1. Using strong passphrases is the most effective thing you can do to prevent cyber crime.
2. Use a strong and separate passphrase for your most valuable accounts, like your home and work email accounts.
3. MFA takes an account from about 50% secure to 99% secure. If it’s available, use it!
4. If you’re struggling to remember multiple passwords, consider a password manager.
Week Two Quiz
For the chance to win a £25 Amazon voucher answer the following question:
Q: What are the three steps to spotting a fake email?
Hint – the answer is in Week Two Part One (see below for a link).
Please send your answers to ISG via https://myservices.ucl.ac.uk/self-service/requests/new/provide_description?from=wizard&service_id=1296&service_instance_id=3679&support_domain=myservices-isg – use the subject line Cyber Security Awareness Month Quiz Entry – Week Two.
Cyber Security Awareness Month – Week Two (Part One)
If you haven’t already read Week Two (Part One), you can find that here: https://blogs.ucl.ac.uk/infosec/2024/10/10/cyber-security-awareness-month-week-two-part-one/
 Close
Close


