Cyber Security Awareness Month – Week One (Part Two)
By Daniela Cooper, on 4 October 2024

Here is Part Two of Week One’s content for Cyber Security Awareness Month. This short security related story is about security incidents. If you haven’t already entered the Week One quiz to win a £25 Amazon voucher, see the details on how to enter at the bottom of the post.
Security incidents
It happened a few days ago. Still, Peter hadn’t told anyone.
As he was sitting in his meeting, he couldn’t stop thinking about it.
“Should I say something? People will judge me. They’ll avoid me. They’ll know.”
So Peter didn’t say a word.
Everyone at his company was affected. And most of his friends. And his friends’ friends, too.
Eventually, 10% of the world’s internet-connected computers were compromised.
What happened to Peter?
Peter received an email with the subject line ILOVEYOU. He opened the attached love letter. This started the malware’s spread.
What’s malware, you might ask?
Malware is malicious software. It’s computer code that can crash devices. It can also steal data, passwords, browsing history and money.

Malware can also lock and delete personal files – which is one of the ways the “ILOVEYOU” malware hurt Peter and its other victims.
After overwriting files, it emailed itself to everyone in Peter’s contact list.
In total, ILOVEYOU caused more than US$15 billion of damage. It left company reputations in tatters.
Bonus content: Six types of malware
Viruses – Viruses attach themselves to normal files. They run when the file is opened. Viruses rely on people sharing infected files to spread.
Worms – Worms are like viruses, but they spread without any human interaction. The most dangerous types replicate across networks. ILOVEYOU was a worm – which is how it affected so many people.
Trojans – Trojans don’t harbour bloodthirsty Ancient Greeks! But they are brutal. Trojans usually open “backdoors” into computers and networks, granting criminals remote access.
Ransomware – Ransomware is worm-like malware that restricts access to files or systems. It then demands victims pay a ransom to regain access. Paying the ransom doesn’t always overcome the infection. Access may be lost forever.
Spyware – Spyware lets criminals spy. It can track what you’re viewing and what you’re typing. Spyware can even turn on webcams and modify security settings.
Grayware – Grayware is software that sits in the “gray” area between malware and software. Think unwanted browser extensions and pop-up ads. Infections pose little direct threat, but they can trigger spontaneous fits of rage.
Was ILOVEYOU avoidable?
It’s unlikely.
But Peter knew about ILOVEYOU early. He could have slowed the spread and reduced the damage it caused.

We can all reduce the impact of malware. It starts with taking responsibility: to prevent, to detect, and to report.
Preventing
Verify emails
If you receive an unexpected email, and you are uneasy about doing something as a result, verify.
Verify by calling back the person you think the message is from. Do so using known contact details.
Check where links lead before clicking
Pro Tip
Found a suspicious site or receive a suspicious email? Report it on the NCSC website and to your IT department.
Show (and check) file extensions
Attachments can contain malware – that’s how Peter’s nightmare started. Some file types are more likely to contain malware than others.
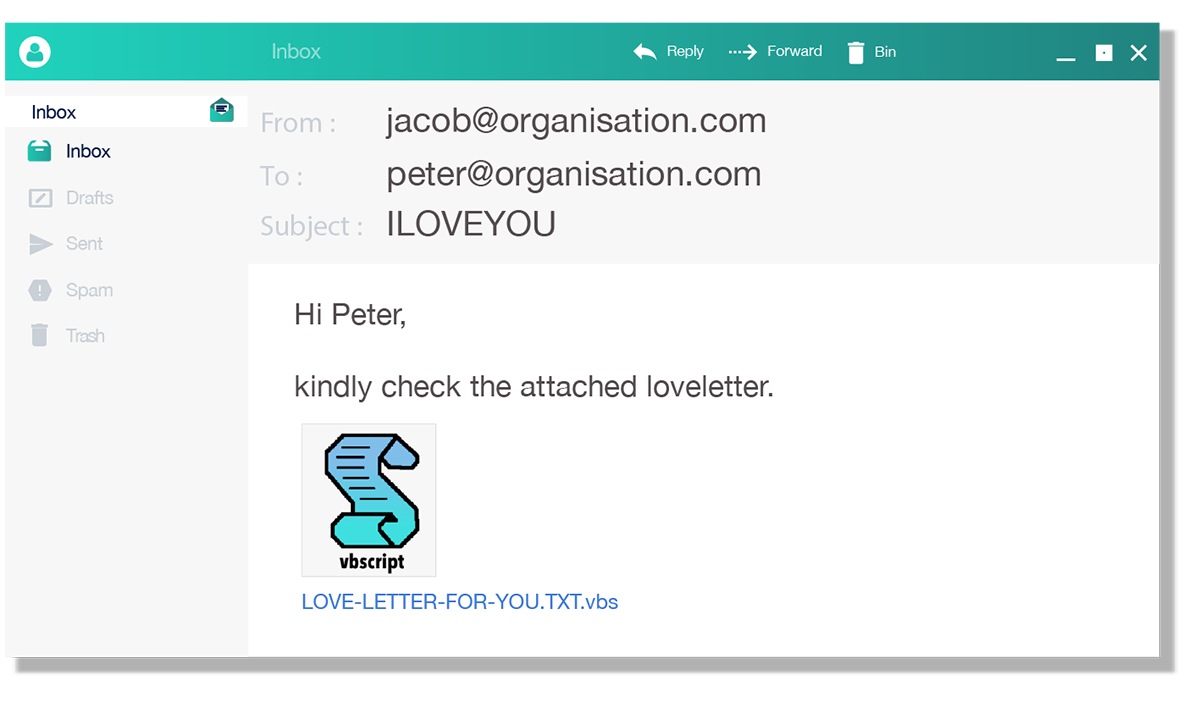
Image description
The image above is a screenshot of an email which contains an attachment with the file extension ‘.vbs’, this attachment is supposedly a love letter.
File extensions are the last three, four or five letters after a filename, like “essay.docx”.
They make dangerous files easier to spot.
File extensions aren’t always displayed by default. If you use a personal device for work, turning on the “Show file extensions” setting will help you to spot dangerous files.
What type of files are dangerous?
All files have the potential to be dangerous. Some are more dangerous than others:
Action files: Files that end with .exe, .vbs or .scr all perform actions when opened or downloaded. They often carry malware.
Macros: Macro-enabled Microsoft Office files can also contain malware. They have an ‘m’ in their file extensions, like “proposal.docm”.
Pro Tip
Microsoft Office will sometimes ask to “Enable macros” or “Turn off protected view”. Doing so can run a series of pre-programmed actions. It’s risky!
Vigilant professionals only open or interact with files they are expecting, and if they know the sender.
Ask for help if you’re ever unsure.
Bonus content: File types
More dangerous:
- Executable – .exe
- Screensaver – .scr
- Visual basic script – .vbs
- MS Word (macro-enabled) – .docxm .docm
- MS Powerpoint (macro-enabled) – .pptxm .pptm
- MS Excel (macro-enabled) – .xlsxm .xlsm
Less dangerous:
- PDF – .pdf .fdf .xfdf
- Image – .jpeg .jpg .png .gif .jp2 .jpx .tif .tiff
- Video – .avi .flv .wmv .mov .mp4
- MS Word (no macros) – .docx .doc
- MS Powerpoint (no macros) – .pptx .ppt
- MS Excel (no macros) – .xlsx .xls
Isolate devices
Malware spreads when devices connect.
Plugging unknown or unauthorised devices into work equipment increases risk. This includes charging cables, USB sticks etc. They can be adapted to carry malware, too.
Refraining from plugging in unauthorised devices – and only charging devices from power sockets – reduces risk.
Download apps safely
Malware can be hidden in useful-looking apps. The apps behave like the real thing while stealing data in the background.
Always download apps from reputable sites like the Apple app store or Google Play. Check reviews before downloading.
Work related software can be downloaded from the UCL Software Database: https://swdb.ucl.ac.uk/
Heed security warnings
Security warnings are the messages displayed by browsers before they allow access to dangerous sites.
Security warnings can be overridden. Doing so is a risk and potentially a breach of policy.
If security warnings restrict access to sites needed for work, letting someone know is the best thing to do (Line manager, IT Team or Security Team). It’s safer and, long-term, will help others in your organisation too.
Detecting
The following can be signs of malware infection:
- People report receiving spam from your email address.
- New icons appear on your desktop or in your web browser.
- Pop-ups appear or programs start running on their own.
- Messages tell you an unknown program is trying to access the internet.
- Your device is unusually slow or crashes at random intervals.
A special mention: Ransomware
Ransomware is worm-like malware that restricts access to files or systems. It then demands victims pay a ransom to regain access. Paying the ransom doesn’t always overcome the infection. Access may be lost forever.
It’s the most destructive and prolific form of malware.
If a device has been infected with ransomware, you’ll likely see a message similar to this:
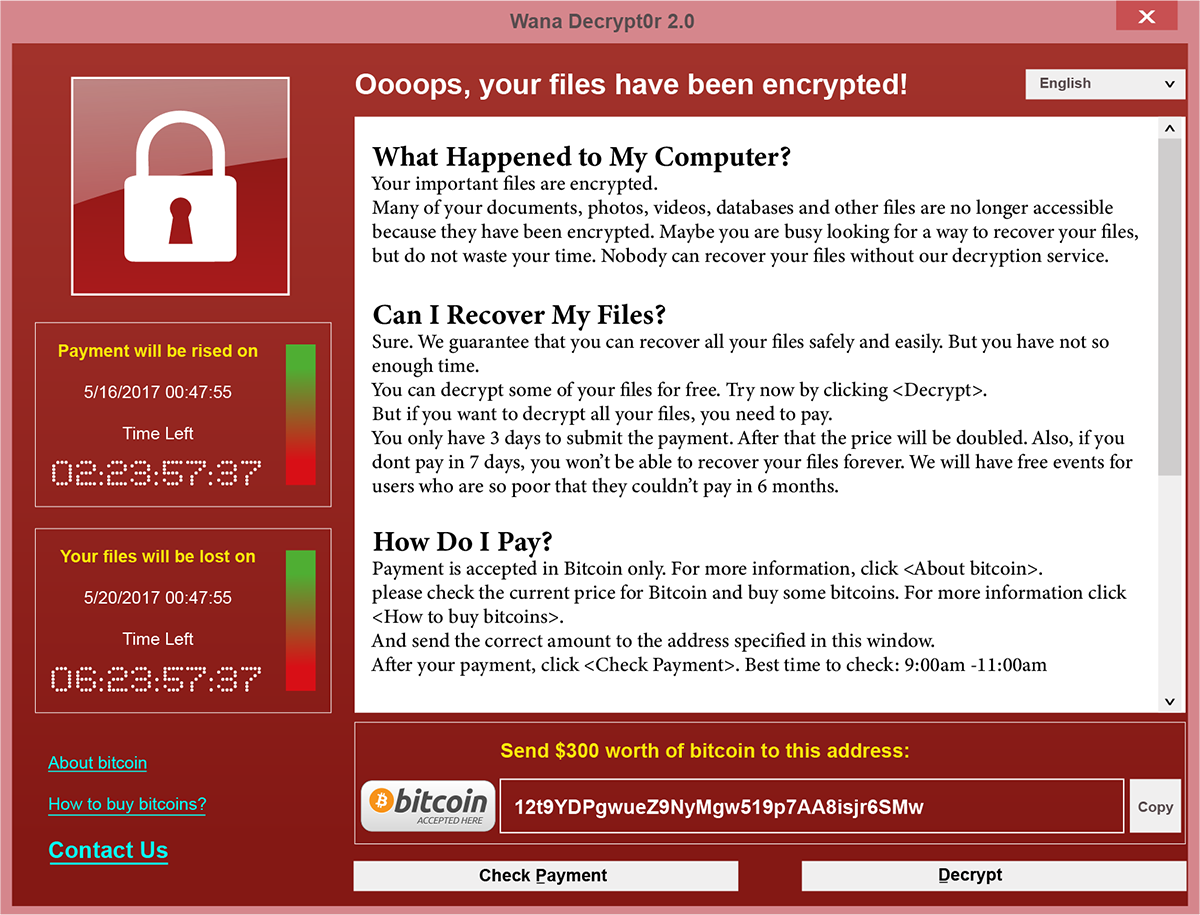
Image description
A large red pop-up containing a ransom note
If you do see a message like this, acting quickly is your chance to make a difference.
Reporting
Reporting security incidents protects organisations from criminals. Still, not all security incidents are reported.
Often it’s because people feel responsible, like Peter. Peter chose not to report so as not to bring attention to himself.
It’s okay to make mistakes. It’s not okay to hide them.
In reality, reporting a security incident is more like a “good catch”. Something happens. You notice it. You report it. Good catch.
Security related incidents should be reported to the UCL Information Security Group via https://myservices.ucl.ac.uk/
Week One Quiz
For the chance to win a £25 Amazon voucher answer the following question:
Q: What percentage of identity thieves use social media to access the personal information of victims?
Please send your answers to ISG via https://myservices.ucl.ac.uk/self-service/requests/new/provide_description?from=wizard&service_id=1296&service_instance_id=3679&support_domain=myservices-isg – use the subject line Cyber Security Awareness Month Quiz Entry – Week One.
Hint: The answer is in Week One (Part One) – see below.
Cyber Security Awareness Month – Week One (Part One)
If you haven’t already read Week One (Part One), you can find that here: https://blogs.ucl.ac.uk/infosec/2024/10/03/cyber-security-awareness-month-week-one-part-1/
 Close
Close


