Cyber Security Awareness Month – Week One (Part One)
By Daniela Cooper, on 3 October 2024

It is that time of year again, where we remind ourselves of the importance of information security in both our personal lives and at work. We are doing things a little differently this year, we will be providing a series of security related short stories using content from CybSafe, there will be two each week. We will still be running the weekly quiz to win a £25 Amazon voucher so make sure you read all the way to the end!
Are you really a target?
BEEP BEEP BEEP BEEP BEEP BEEP. SLAM.
The sound of Joe turning off his fifth alarm.
It’s 7 a.m. and a brand new day. Time to get up and get out. He throws on a shirt and tie, brushes his teeth, and wakes up the kids.
“Myles, Lily, time to wake up!”
“But bed is so comfy!”
“Up!”
Joe heads downstairs, puts on his ‘Morning tunes’ and packs their lunches. When Myles and Lily eventually grace the kitchen table, Joe snaps a cute pic of them eating breakfast.
Little does Joe know, he’s already a target. And not because of his music taste.
How do you like your eggs in the morning?
Joe posts the picture on social media: ‘my two little eggs <3’
“Dad, you’re so embarrassing!”
“And your profile isn’t even private!” …

Joe’s social media profile catches the eye of a fraudster.
Everything about Joe is public. His music, birthday, friends, family, job title, company, email address, phone number and favourite wrestler. You name it, it’s there.
85% of identity thieves use social media to access victims’ personal information.
As Joe coaxes Lily and Myles out of the house, the fraudster is hard at work. There is so much information about Joe available online, it’s a matter of moments before the fraudster has loaded everything into a password profiler.
Within minutes, the fraudster has access to Joe’s accounts. Netflix, Amazon, Facebook, Instagram, LinkedIn, the lot.
As Joe drops Lily and Myles at school, the fraudster is selling Joe’s Netflix account on the dark web.
This is really going to mess with his TV recommendations.
Pro Tip
Fraudsters view public social media profiles as one thing: $$$.
Find out what information about you is publicly available by using a search engine. Fraudsters use personal information to access accounts, so it’s best to keep them private. Just log onto your social media accounts and change the privacy settings. After all, there’s nothing more off-putting to a fraudster than a private account.
Coffee, anyone?
Joe arrives at work, makes his way to his desk and turns on his laptop. He is confronted by something that strikes fear into his heart: update notifications.
System, antivirus and app updates! When will they end?
But Joe knows how to deal with these pesky notifications: ignore them till they go away.
He knows that it takes roughly 10 minutes for them to disappear. He sticks his head out into the office. “Coffee, anyone?”
Pro Tip
Forgetting to install updates to your devices or applications is like leaving your front door unlocked. Updates allow security improvements to be applied. Without updates, your device is vulnerable to compromise and puts confidential data at risk.
You can set updates to automatically install in your device’s security settings.
One watercooler chat and cappuccino later, Joe returns to his desk. No more notifications. It’s like magic. He settles down and opens his emails.
Joe doesn’t realise that he’s a dream come true. At least, he is for organised crime groups. He has access to data and information that can be sold for a profit. And what’s more, he skips security updates.
As Joe opens up his emails, he sees a message from the CEO.
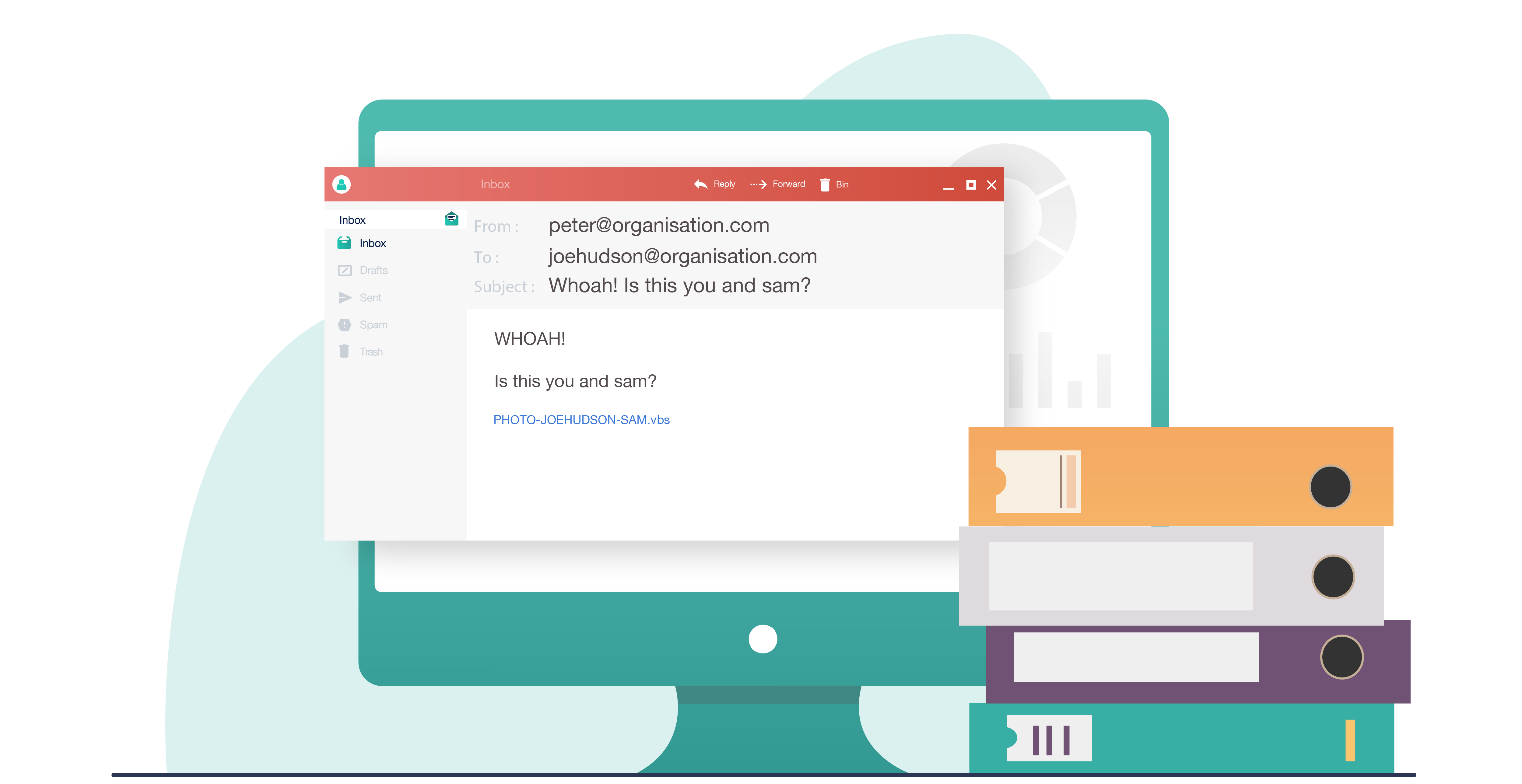
The message has an attachment. It appears to contain a picture of Joe and the Director of Marketing, Sam. Nerve-wracking stuff to receive from the CEO.
In a panic, Joe forwards the email to Sam and clicks on the attachment. There is no picture.
Joe, confused, wipes his brow and laughs it off. Little does he know, spyware has started taking over his laptop.
Case study: It makes you WannaCry
The WannaCry attack was run by state-sponsored criminals. It affected over 200,000 computers in 150 countries with an estimated global cost of USD $12 billion.
Malicious software was delivered via emails tricking recipients into opening an attachment. Once opened, the software restricted information and data, demanding payment to reinstate access.
Pro Tip
Verify! Verify! Verify!
Using known contact details to verify emails and messages is an easy way to avoid malicious attachments. When in doubt, verify! Especially before forwarding anything.
And be sure to check if any attached files end in ‘.exe’, ‘.vbs’ or ‘.scr’. These file types perform an action which could put your device at risk.
Across the office, Sam receives the email and opens the attachment. A warning flashes onto his screen: ‘this attachment is unsafe.’
Sam’s laptop had been set to auto-update. Thankfully, the most recent update contained a defence against new internet nasties. It was installed while Sam was chatting to Joe by the watercooler.
Sam reported the email straight away. Crisis averted.
Afternoon delight
Nothing is nicer than a well-deserved lunch break. And Joe’s lunch break is positively delightful. He’s meeting an old co-worker for fajitas.
The Head of IT’s afternoon is also delightful. She prevented an attack by removing a load of spyware that somehow found its way into the system. Weird.
Pro Tip
Refer! Refer! Refer!
Referring any suspicious messages, emails or attachments to your IT department can help prevent future attacks and identify sneaky malware.
Joe sits down and orders some fajitas. Robin, Joe’s ex-coworker, sits down beside him. After some witty repartee, Robin shifts the topic of conversation.
“I was wondering if you could get me back into the office? I left a few bits I need to grab.”
“Of course! We can head there after lunch.”

Insiders love access. For malicious employees, access is an opportunity for exploitation. And who better to grant it than a trusting soul like Joe?
Pro Tip
Insiders often try to intercept information or obtain documents requiring elevated access. Everyone has the power to challenge access.
You should feel authorised to question people when you are unsure of something. Someone in the office without a pass? Ask to see it. Someone requesting to view a confidential document? Verify their reason.
Back at work, Robin follows Joe into the office. Sam thinks it’s a bit odd, but doesn’t question it.
“Just going to grab my stuff.” Robin whispers, heading into the backroom. Joe nods and gets back to work. Meanwhile, Sam does a quick LinkedIn search. Robin is now working for their competitor.
“Erm… Joe?”
“Yes, Sam?”
“Did you know Robin works for our competitor?”
Joe’s eyes widen as he realises that Robin could be an insider.
Joe rushes into the back office. There stands Robin. He’s taking photos of important documents.
And he would have gotten away with it too…
Case study: Employee of the month
For one credit card provider, it only took a disgruntled employee to wreak havoc. The insider managed to steal the personal data of 100 million US citizens as they knew where it was stored. It cost the company approx. USD $100-150 million to fix.
A hard day’s night
After a long day of being a target, Joe just wants to watch TV with his kids. But as he logs in to Netflix, something seems off.
“Which one of you has been watching Dance Moms?”
Myles and Lily shrug their shoulders, “not us!”
“And which one of you has made a new profile?”
“What new profile?”
Joe clicks back to the profile selection page.
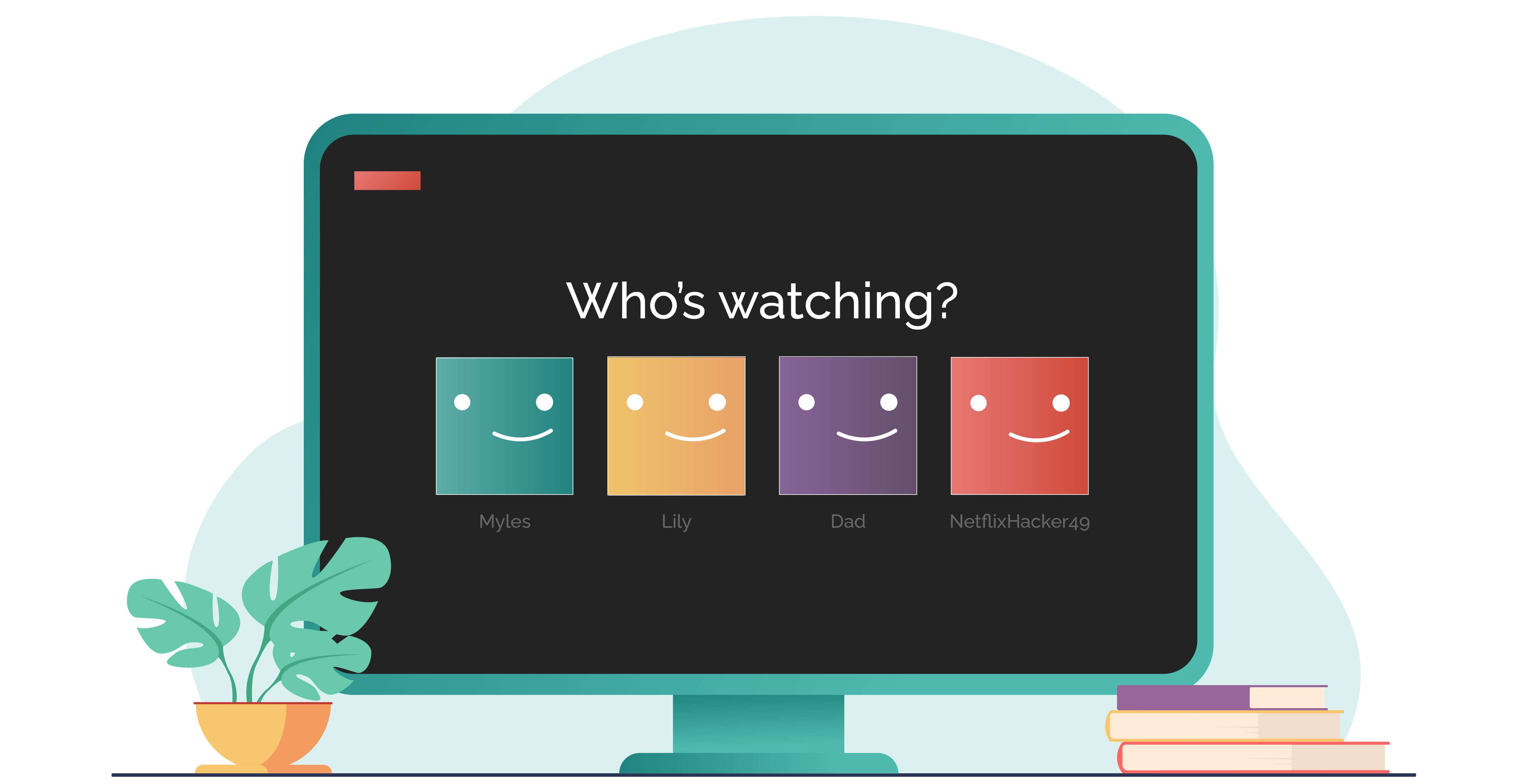
“There! Which one of you is NetflixHacker49?”
Myles and Lily give another shrug.
Joe realises what has happened. His account has been hacked. And if this account is compromised, others might be too. Joe gives Sam a ring.
“I think my Netflix account has been hacked!”
“Okay, calm down.”
Sam sends Joe a message that contains a single line:
“Go on that website and type in your email,” Sam explains, “it’ll tell you if there’s been a breach.”
With a flurry, Joe types in his details and hits ‘Enter’.
Oh no – pwned!
Joe’s accounts have been breached. “Not to worry” Sam calmly states. “Go into your accounts and change your passwords to separate passphrases.”
Joe hands the remote control to Myles and jumps on his computer.
As he goes through his accounts, Lily’s voice drifts in from the living room.
“Daaaad!”
“Yes, Lily?”
“Myles has clicked on something he shouldn’t have!”
Here we go again.

Summary
1. No matter your job description, role or department, YOU are responsible for keeping your organisation’s data safe. Cyber security is for everyone, not just the tech-savvy people in IT!
2. Stopping yourself from becoming a target requires little added effort. A few quick changes can set you up for success.
3. Reporting potential infections or issues can make you a security hero. It gives your organisation a chance to act quickly and respond. If they can respond quickly, they can limit the damage.
4. Be more like Sam.
Week One Quiz
For the chance to win a £25 Amazon voucher answer the following question:
Q: What percentage of identity thieves use social media to access the personal information of victims?
Please send your answers to ISG via https://myservices.ucl.ac.uk/self-service/requests/new/provide_description?from=wizard&service_id=1296&service_instance_id=3679&support_domain=myservices-isg – use the subject line Cyber Security Awareness Month Quiz Entry – Week One.
Cyber Security Awareness Month – Week One (Part Two)
If you haven’t already read Week One (Part Two), you can find that here: https://blogs.ucl.ac.uk/infosec/2024/10/04/cyber-security-awareness-month-week-one-part-two/
 Close
Close


